In this tutorial i’m going to learn how to secure your PHP project.
1 Update PHP Regularly
One of the cardinal rules of PHP security is to stay up-to-date. PHP has had its share of security vulnerabilities in the past, but diligent efforts by the community and maintainers have led to frequent updates and patches. Make sure you are using the latest version of PHP to benefit from security improvements. It is recommended that you update to this new PHP application. When updating PHP applications, you will encounter numerous deprecations if you are still running PHP 5.6 or 7. It will also be necessary for you to update your code and modify some functional logics, such as hashing passwords, etc.
Why We need to do this PHP update Regularly ?
There are three main reasons why you need to update your PHP version regularly:
Security: Newer versions of PHP are regularly patched against security vulnerabilities. If you are running an outdated version of PHP, your website is more likely to be hacked.
Performance: Newer versions of PHP often include performance improvements, which can make your website load faster and use less memory.
New features: Newer versions of PHP also include new features and improvements, which can make it easier to develop and maintain your website.
Security thread if i ignore this Updated PHP ?
Ignoring PHP updates, especially security updates, can pose significant security threats to your web applications and server environment. Here are some potential security risks associated with not updating PHP:
- Vulnerabilities and Exploits: Outdated PHP versions may contain known vulnerabilities that hackers can exploit. Security updates often include patches to address these vulnerabilities and protect your applications from being compromised.
- Malicious Attacks: Cybercriminals actively target outdated software. If they discover a vulnerability in an older PHP version, they may launch attacks to exploit these weaknesses, potentially leading to unauthorized access, data breaches, or other security incidents.
- Data Breaches: A compromised PHP environment can result in unauthorized access to sensitive data. This could lead to data breaches, exposing confidential information, user credentials, or other critical data.
2. Disable ‘allow_url_fopen‘
What is allow_url_fopen ?
PHP allows including files from remote URLs using the ‘allow_url_fopen’ directive. This feature can be manipulated by attackers for cross-site scripting (XSS) or arbitrary command execution attacks. To prevent this, disable ‘allow_url_fopen’ in your ‘php.ini’ configuration file.
If you need to enable allow_url_fopen for your scripts, you can do so by editing your php.ini file. Find the line that says allow_url_fopen = Off and change it to allow_url_fopen = On. Then, restart your web server for the changes to take effect.
Security thread if i ignore this allow_url_fopen ?
Ignoring the allow_url_fopen configuration and enabling the ability to open remote files in PHP scripts can introduce security risks. Here are some potential threats associated with allowing allow_url_fopen:
- Remote Code Execution (RCE):
- Allowing remote file inclusion may lead to remote code execution vulnerabilities. An attacker could provide a malicious URL that points to a script containing code to be executed on your server.
- Arbitrary File Access:
- Enabling
allow_url_fopenallows PHP scripts to read files from remote servers. If an attacker can control the URL, they might be able to access sensitive files on other servers.
- Enabling
Example :-
<?php
// Enable allow_url_fopen
ini_set('allow_url_fopen', true);
// Open the remote file for writing
$fp = fopen('https://example.com/upload.php', 'w');
// Write the contents of the file to the remote server
fwrite($fp, file_get_contents('myfile.txt'));
// Close the remote file
fclose($fp);
?>3. Disable ‘register_globals’
What is register_globals ?
register_globals is a PHP configuration directive that, when enabled, automatically turns global variables into PHP variables. This means that variables from various sources, such as form inputs, cookies, and server variables, are automatically converted into global variables.
Security thread if i ignore this register_globals ?
Ignoring the security implications of register_globals in PHP can lead to various vulnerabilities and pose significant risks to your application. Here are some of the security threats associated with ignoring or enabling register_globals:
- Variable Injection and Manipulation:
- Enabling
register_globalsallows external input (such as form data or query parameters) to be automatically transformed into global variables. This can lead to variable injection, where an attacker manipulates variables by controlling input values, potentially causing unintended consequences in the application.
- Enabling
- Security Exploits:
- Automatically converting input data into global variables increases the risk of security exploits, including SQL injection, cross-site scripting (XSS), and other injection attacks. Attackers may manipulate input fields to inject malicious code into the application.
Example :-
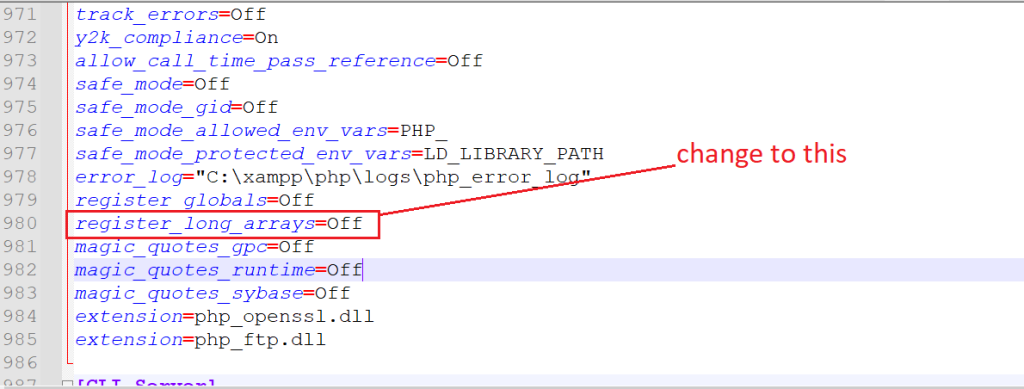
Go to php.ini and put below code
register_globals = Off
4. Restrict access to sensitive files
Certain files on your web server should be restricted to only trusted users. These files could include the configuration file, database credentials, or source code files. By restricting access to these files, you can help prevent attackers from gaining access to sensitive information.
5. PHP Object Injection
With the PHP object injection attack, an attacker calls the unserialize() function with unsanitized user inputs to inject PHP objects into memory. A successful PHP object injection attack can result in further attacks like SQL Injection, Path Traversal, or even the complete web application shutdown.
How to Prevent PHP Object Injection Attack?
To prevent PHP object injection attacks, verify and sanitize each input your web application receives. It would ensure no PHP objects are submitted and your application is safe.
6. Validating and sanitizing data
Validating and sanitizing data in PHP are two important steps in preventing security vulnerabilities and ensuring that your data is accurate and consistent.
Validation is the process of checking data to make sure that it meets certain criteria. For example, you might validate a user’s email address to make sure that it is in a valid format.
Sanitization is the process of removing any harmful or malicious characters from data. For example, you might sanitize user input to remove any HTML code or SQL injection characters.
PHP provides a number of functions for validating and sanitizing data. The most common function is filter_var(). This function can be used to validate and sanitize a variety of different data types, including strings, integers, and floats.
Example :-
// Validate the user's name and email address.
$name = filter_var($_POST['name'], FILTER_SANITIZE_STRING);
$email = filter_var($_POST['email'], FILTER_VALIDATE_EMAIL);
// If the name or email address is invalid, display an error message.
if ($name === false || $email === false) {
echo "Error: Invalid name or email address.";
exit();
}
// Sanitize the user's message.
$message = filter_var($_POST['message'], FILTER_SANITIZE_STRING);
// Insert the sanitized data into the database.
$sql = "INSERT INTO users (name, email, message) VALUES (:name, :email, :message)";
$stmt = $db->prepare($sql);
$stmt->bindParam(':name', $name);
$stmt->bindParam(':email', $email);
$stmt->bindParam(':message', $message);
$stmt->execute();
// Success!
echo "Your message has been sent successfully.";7. Use the Strict-Transport-Security Header
What is Strict-Transport-Security header ?
The Strict-Transport-Security header ensures that the browser does not talk to the server over HTTP. This helps reduce the risk of HTTP downgrade attacks as implemented by the sslsniff tool.
Security thread if i ignore Strict-Transport-Security Header ?
Ignoring the Strict-Transport-Security (HSTS) header in PHP can introduce security vulnerabilities, particularly related to man-in-the-middle attacks and data interception. HSTS is a web security policy mechanism that helps protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking.
Here are some security threats associated with ignoring the Strict-Transport-Security header:
- Man-in-the-Middle Attacks:
- Without HSTS, an attacker could potentially intercept and modify communication between the client and server by downgrading the connection to HTTP or performing other types of attacks.
- Cookie Hijacking:
- HSTS helps prevent session hijacking and cookie theft by ensuring that communication between the client and server occurs over a secure, encrypted connection (HTTPS).
- Session Fixation:
- Without HSTS, attackers may attempt session fixation attacks by intercepting an initial unencrypted connection and then forcing the victim to use the compromised session.
Example :-
Header set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"8. Cross-site scripting (XSS)
What is Cross-site scripting (XSS) ?
Cross-Site Scripting (XSS) is a security vulnerability that can occur in PHP and other web applications. XSS occurs when an attacker injects malicious scripts into web pages that are then viewed by other users. These scripts are typically written in JavaScript, but other scripting languages can also be used.
Security thread if i ignore Cross-site scripting (XSS) ?
Cross-site scripting (XSS) is a type of web security vulnerability that allows an attacker to inject malicious code into a website. This code can then be executed by the victim’s browser when they visit the website.
XSS attacks can be used to steal the victim’s cookies, redirect the victim to another website, or even execute malicious code on the victim’s computer.
If you ignore XSS in PHP, you are putting your website and your users at risk. Here are some of the security threats that you could face:
- Stolen cookies: An attacker could use XSS to steal a user’s cookies, which could then be used to impersonate the user and access their account.
- Redirects: An attacker could use XSS to redirect a user to another website, such as a phishing website or a website that contains malware.
- Malicious code execution: An attacker could use XSS to execute malicious code on the victim’s computer, such as a virus or a Trojan horse.
Example :-
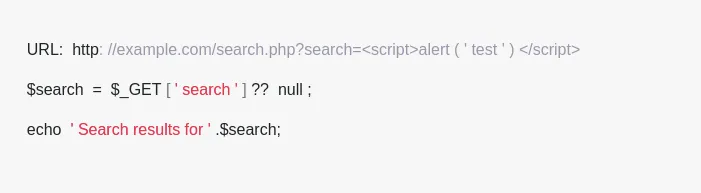
9. SQL Injection Attacks
What is SQL injection Attacks ?
SQL injection attacks are a type of web security vulnerability that allows an attacker to inject malicious code into a website’s SQL queries. This code can then be executed by the database server, which can give the attacker access to the database’s data or even allow them to take control of the database server.
Security thread if i ignore SQL injection Attacks ?
SQL injection attacks are a serious security threat to any website that uses a database. PHP is a popular programming language for developing websites, and it is important to be aware of the security risks associated with using PHP.
If you ignore SQL injection attacks in PHP, you are putting your website and your users at risk. Here are some of the security threats that you could face:
- Stolen data: An attacker could use SQL injection to steal data from your database, such as user names, passwords, and credit card numbers.
- Altered or deleted data: An attacker could use SQL injection to alter or delete data in your database. This could damage your database and disrupt your business operations.
- Database server takeover: In some cases, an attacker could use SQL injection to take control of your database server. This could give the attacker access to all of the data on your server, and could even allow them to launch attacks against other websites.
In SQL injection attack, the attacker tries to alter the data you are passing via queries. Suppose you are directly processing user data in SQL queries, and suddenly, an anonymous attacker secretly uses different characters to bypass it. See the below-mentioned SQL query:
Example:-
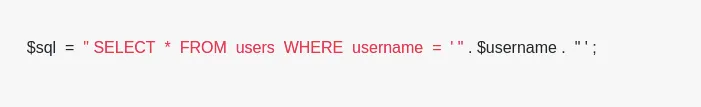
10. Log all Errors and Hide in Production
What is Log all errors ?
Logging all errors in PHP is an essential practice for debugging and monitoring the health of your web application. PHP provides a configuration directive called error_log that allows you to specify the destination for error logging.
Security thread if i ignore this Log all errors ?
Ignoring the practice of logging all errors in PHP can expose your web application to several security threats and operational challenges. Here are some security risks and drawbacks associated with neglecting error logging:
- Lack of Visibility into Issues:
- Without error logging, you may miss crucial information about issues and errors occurring in your application. This lack of visibility can lead to undetected security vulnerabilities and operational problems.
- Difficulty in Debugging:
- When errors occur, especially in production environments, debugging becomes challenging without detailed error logs. Identifying the root cause of issues becomes a time-consuming and complex process.
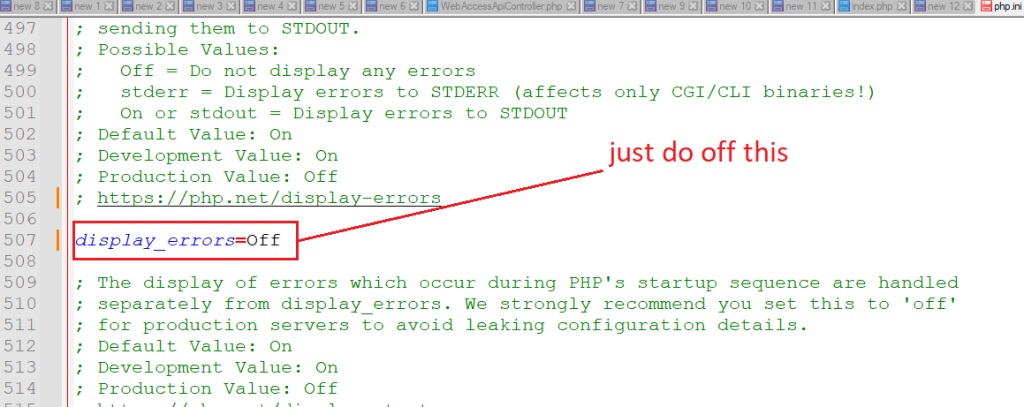
Example :-
Go to php.ini and do paste below code
display_errors=Off
11. Session Hijacking
What is Session hijacking ?
Session hijacking, also known as session stealing or session hijacking, is a security attack in which an unauthorized user gains access to a legitimate user’s session. In the context of PHP and web applications, sessions are used to maintain user-specific information across multiple requests, and session hijacking occurs when an attacker takes control of a user’s active session.
Security thread if i ignore Hijacking ?
If you ignore session hijacking in PHP, you are putting your website and your users at risk. Here are some of the security threats that you could face:
- Account takeover: An attacker could use session hijacking to take control of a user’s account. This could give the attacker access to the user’s personal information, financial information, and other sensitive data.
- Fraud: An attacker could use session hijacking to make fraudulent transactions on behalf of a user. This could include making unauthorized purchases, transferring money, or even stealing the user’s identity.
- Data breaches: An attacker could use session hijacking to access sensitive data on your website, such as customer records, financial data, or even intellectual property.
- Malware distribution: An attacker could use session hijacking to distribute malware to your users. This could infect the user’s computer with a virus, Trojan horse, or other type of malware.
Example :-
To prevent session hijacking always bind sessions to your IP address to:
$IP = getenv ( "REMOTE_ADDR" );
12. Use secure password storage mechanisms
Password security is a critical aspect of PHP website security. It is important to use secure password storage mechanisms to protect user passwords from being easily decrypted by attackers. This can help prevent unauthorized access to user accounts and protect sensitive information.
Why We need to do this Secure Password ?
One commonly used secure password storage mechanism is bcrypt. Bcrypt is a password-hashing function that is designed to be slow and computationally intensive, making it difficult for attackers to brute-force passwords. Bcrypt also includes a salt, which is a random value added to the password before hashing, making it more difficult for attackers to crack the password using precomputed tables.
When using bcrypt for password storage, it is important to use a high enough number of iterations to make brute-force attacks infeasible. The number of iterations used is known as the “work factor” and should be adjusted based on the resources available on the server.
Other secure password storage mechanisms include Argon2, PBKDF2, and scrypt. These mechanisms are also designed to be slow and computationally intensive, making it difficult for attackers to brute-force passwords.
Example :-
function hashPassword($password) {
// Generate a random salt
$salt = bin2hex(random_bytes(22));
// Hash the password using bcrypt with the salt
$hashedPassword = password_hash($password . $salt, PASSWORD_BCRYPT);
// Return the hashed password and salt
return [
'hashedPassword' => $hashedPassword,
'salt' => $salt,
];
}13. Limit File Uploads
What is Limit File Uploads ?
Limiting file uploads is an important security measure to protect your PHP website from potential attacks. File uploads can be a major security risk, as malicious files can be uploaded to your server and executed, causing harm to your website and potentially compromising sensitive information.
Why We need to do this Limit File Uploads ?
Limiting file uploads in PHP is an important security practice that helps protect your web application from potential threats and misuse. Here are several reasons why limiting file uploads is necessary:
- Prevent Denial of Service (DoS) Attacks:
- Without file upload limits, an attacker could flood your server with large or numerous files, causing a denial of service. Limiting file sizes helps mitigate the impact of DoS attacks.
- Mitigate Storage Abuse:
- Unrestricted file uploads can lead to storage abuse, where users upload excessive or large files, consuming server storage resources. This can result in increased hosting costs and degraded server performance.
- Avoid Exhausting Server Resources:
- Processing large file uploads requires server resources, such as memory and processing power. Limiting file sizes helps prevent resource exhaustion, ensuring the smooth operation of your application.
Example :-
<?php
$maxFileSize = 5 * 1024 * 1024; // 5 MB
if ($_FILES['file']['size'] > $maxFileSize) {
// File size exceeds the limit
echo "File size exceeds the limit.";
} else {
// Process the file upload
move_uploaded_file($_FILES['file']['tmp_name'], 'uploads/' . $_FILES['file']['name']);
echo "File uploaded successfully.";
}
?>14. Use Captcha
What is Captcha ?
A CAPTCHA is a type of challenge-response test used in computing to determine whether the user is a human or a bot. The test is typically a distorted image of text or letters that the user must type into a field. CAPTCHAs are often used on websites to prevent bots from creating accounts or submitting spam.
To implement a CAPTCHA in PHP, you can use the following steps:
- Install a CAPTCHA library for PHP. There are many different libraries available, such as recaptchalib, captcha-lib, and captcha.php.
- Create a new PHP script and generate a CAPTCHA image using the library you installed.
- Display the CAPTCHA image on your website and ask the user to type in the text or letters they see.
- Verify the user’s response using the CAPTCHA library.
Security thread if i ignore Captcha ?
Ignoring CAPTCHAs in PHP can be a security threat for your website. CAPTCHAs are used to prevent bots from creating accounts or submitting spam. If you ignore CAPTCHAs, bots will be able to freely create accounts on your website and submit spam to your contact form or other forms. This can lead to a number of security issues, such as:
- Account takeover: Bots can create accounts on your website using stolen email addresses and passwords. Once they have created an account, they can use it to steal your data or post malicious content.
- Spam: Bots can submit spam to your contact form or other forms. This can waste your time and resources, and it can also damage your reputation.
- Distributed denial-of-service (DDoS) attacks: Bots can be used to launch DDoS attacks against your website. This can make your website unavailable to legitimate users.
Example :-
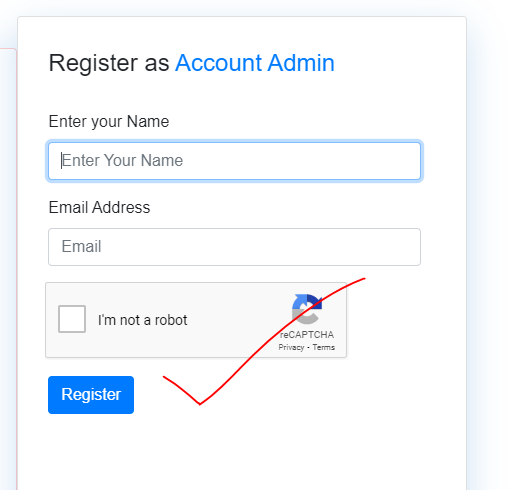
15. Use two-factor authentication
What is two-factor authentication ?
Two-factor authentication (2FA) adds an extra layer of security to your authentication process by requiring users to provide a second factor, such as a code generated by an app or sent via email.
Why We need to do two-factor Authentication ?
There are a number of reasons why you should implement two-factor authentication (2FA) in your Laravel application:
- Improved security: 2FA adds an extra layer of security to your application, making it more difficult for attackers to gain access to user accounts. Even if an attacker is able to obtain a user’s password, they will still need the second factor code to log in.
- Reduced fraud: 2FA can help to reduce fraud, such as unauthorized account takeovers and fraudulent transactions. By requiring users to enter a second factor code to log in, you can make it more difficult for attackers to commit these types of fraud.
Security thread if i ignore two-factor Authentication ?
If you ignore two-factor authentication (2FA) in Laravel, you may be opening your application up to a number of security threats, including:
- Unauthorized access to sensitive data: If an attacker is able to gain access to a user’s account, they may be able to access sensitive data, such as financial information, personal information, or intellectual property. 2FA can help to protect sensitive data by making it more difficult for attackers to gain access to user accounts.
16. Session Hijacking
What is Session Hijacking ?
Session hijacking is a type of cyberattack where an attacker steals a user’s session identifier, also known as a session ID. A session ID is a unique identifier that is used to track a user’s activity on a website or web application. Once the attacker has the session ID, they can impersonate the user and gain access to their account.
How to fix it?
- Regenerate the session ID after a user authenticates, logs in, or changes privilege levels.
- Enhance PHP security by implementing secure session handling techniques such as using secure cookies, enabling HTTP-only flags, and configuring appropriate session options.
Example :-
<?php
session_id('attacker_session_id'); // Set the session ID to the attacker's session ID
session_start();
// Perform malicious actions
?>17. Insecure Direct Object References (IDOR)
What is Insecure Direct Object References ?
An insecure direct object reference (IDOR) is a type of security vulnerability that occurs when a web application allows users to directly access objects without checking whether they have permission to do so. This can be done by exposing object identifiers in URLs, request parameters, or response data.
Security thread if i ignore this Insecure Direct Object References ?
Ignoring Insecure Direct Object References (IDOR) vulnerabilities in PHP can lead to various security threats and compromise the confidentiality, integrity, and availability of your application and its data. Here are some potential security threats and consequences associated with neglecting IDOR vulnerabilities:
- Unauthorized Data Access:
- Attackers can exploit IDOR vulnerabilities to access sensitive data or resources they are not authorized to view. This may include accessing other users’ information, confidential documents, or administrative functionalities.
- Data Manipulation:
- In addition to unauthorized access, IDOR vulnerabilities can allow attackers to manipulate or modify data. For example, an attacker might change the user ID in a URL parameter to modify someone else’s profile information.
- Exposure of Confidential Information:
- IDOR vulnerabilities can lead to the exposure of confidential information, such as financial records, personal details, or proprietary data. This exposure can have legal and reputational consequences for the organization.
- Loss of Data Integrity:
- Manipulation of data through IDOR attacks can lead to the loss of data integrity. For example, an attacker might alter the contents of a database, leading to inaccurate or corrupted data.
Example :-
<?php
$id = $_GET['id']; // User-supplied input for fetching an object
$query = "SELECT * FROM products WHERE id = $id"; // Insecure direct object reference
$result = mysqli_query($connection, $query);
$product = mysqli_fetch_assoc($result);
// Display product details
?>18. Get SSL Certificate for the php Website
What is SSL Certificate ?
SSL certificates offer security by initiating encrypted sessions. Unlike HTTP connections, where communications happen in a textual format, HTTPS communications happen via ciphertexts. Therefore, one will need a decryption key to access encrypted data. Hackers, eavesdroppers, prying eyes and other parties that do not mean well to the app and its data are thus locked up from communications.
For top security of your Laravel application, you will need to buy and install an SSL certificate. The SSL certificate is available at low price like single-domain certificate, cheap multi-domain SSL certificate, low cost wildcard SSL certs, all of which will play in favour of your Laravel security.
Security thread if i ignore SSL Certificate ?
If you ignore SSL certificate, you will be exposing your application to a number of security threats, including:
- Man-in-the-middle attacks: A man-in-the-middle attack is an attack where an attacker intercepts communication between two parties and impersonates one of the parties. If you are not using SSL, attackers can easily perform man-in-the-middle attacks on your application.
- Eavesdropping: Eavesdropping is an attack where an attacker listens to communication between two parties. If you are not using SSL, attackers can easily eavesdrop on communication between your application and your users.
- Replay attacks: A replay attack is an attack where an attacker intercepts a message and then replays it later. If you are not using SSL, attackers can easily perform replay attacks on your application.
- Data breaches: If an attacker is able to intercept communication between your application and your users, they may be able to steal sensitive data, such as passwords, credit card numbers, and personal information.
Example :-
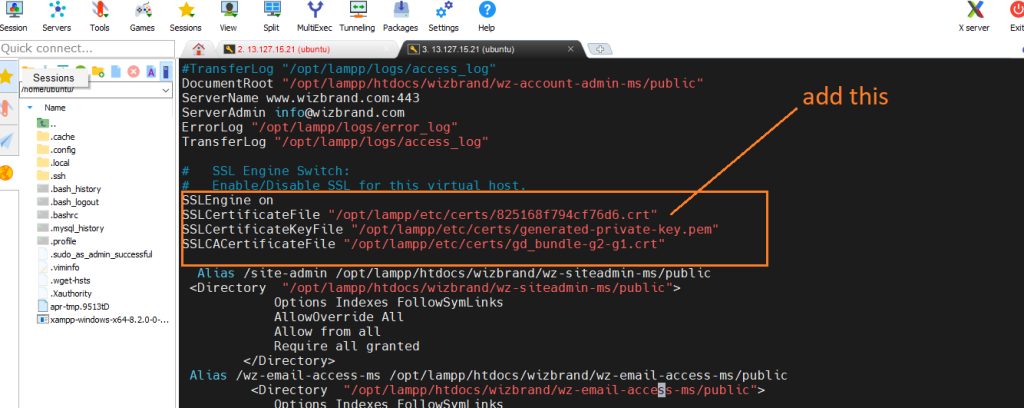
a. First download ssl certificate
b. got to /opt/lampp/etc/extra/httpd-ssl.conf
And add your certification path there
19. Un-validated user inputs
Must validate all user inputs
A common PHP security flaw is not validating user inputs submitted via forms or as arguments in url strings. You must never trust data provided in online forms by users and site visitors. There is a good number of people sitting out there on the internet who have no other job than to keep attempting to damage others work. Un-validated or improperly validated input is one of the root causes of many of the exploits.
Example :-
$month = $_GET['month'];
$year = $_GET['year'];
exec("cal $month $year", $result);
foreach($result as $r) print "$r"; 20. Enable Mod-security2
What is Mod-security2 ?
ModSecurity, often referred to as mod_security or mod_security2, is an open-source web application firewall (WAF) module that is typically deployed with the Apache HTTP Server. It provides a set of tools for monitoring and securing web applications by applying various security rules and policies.
Why We need to do this Mod-security2 ?
Implementing ModSecurity, or ModSecurity2, is beneficial for several reasons, especially when it comes to enhancing the security posture of web applications and protecting against various cyber threats. Here are some key reasons why organizations use ModSecurity:
- Protection Against Web Application Attacks: ModSecurity acts as a web application firewall (WAF), providing protection against a wide range of web application attacks, including SQL injection, cross-site scripting (XSS), and other common vulnerabilities. It helps to filter malicious traffic before it reaches the web application.
- Prevention of SQL Injection and Cross-Site Scripting: SQL injection and XSS are common attack vectors where attackers attempt to inject malicious code into web applications. ModSecurity can detect and prevent these types of attacks by analyzing and filtering incoming requests.
- Security Compliance: Many regulatory standards and security best practices recommend or require the implementation of a WAF for web applications. ModSecurity helps organizations achieve and maintain compliance with standards such as PCI DSS (Payment Card Industry Data Security Standard) and others.
- Real-time Monitoring and Incident Response: ModSecurity provides real-time monitoring of web traffic and logs security events. This allows security teams to analyze and respond to incidents promptly. The detailed logging helps in identifying the nature of attacks and understanding the security posture of the web application.
Security thread if i ignore Mod-security2
If your’re Ignoring ModSecurity2 then your web applications vulnerable to a range of security threats. Here are some potential security threats and risks associated with not using ModSecurity2:
- SQL Injection Attacks: Without a WAF like ModSecurity, your web applications may be susceptible to SQL injection attacks. Attackers can inject malicious SQL queries into input fields, potentially leading to unauthorized access, data manipulation, or data theft.
- Cross-Site Scripting (XSS) Attacks: XSS attacks involve injecting malicious scripts into web pages viewed by other users. Without protection, your applications may be vulnerable to these attacks, which can lead to session hijacking, defacement, or the theft of sensitive information.
- Cross-Site Request Forgery (CSRF) Attacks: CSRF attacks involve tricking a user’s browser into making unintended requests. ModSecurity can help detect and prevent these attacks by validating and blocking malicious requests.
- Security Compliance Violations: Many regulatory standards and compliance requirements mandate the use of a web application firewall. Ignoring ModSecurity may lead to non-compliance with standards such as PCI DSS, exposing your organization to potential legal and financial consequences.
Installation of ModSecurity:
sudo apt install libapache2-mod-security2
Run below code
sudo a2enmod security2
nano /etc/apache2/mods-enabled/security2.conf<IfModule security2_module>
# Default Debian dir for modsecurity's persistent data
SecDataDir /var/cache/modsecurity
# Include all the *.conf files in /etc/modsecurity.
# Keeping your local configuration in that directory
# will allow for an easy upgrade of THIS file and
# make your life easier
IncludeOptional /etc/modsecurity/*.conf
# Include OWASP ModSecurity CRS rules if installed
IncludeOptional /usr/share/modsecurity-crs/*.load
</IfModule>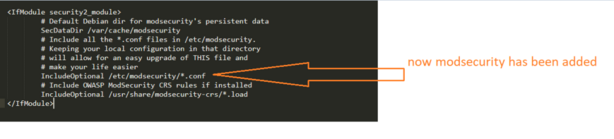
sudo mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
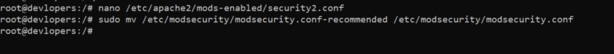
sudo nano /etc/modsecurity/modsecurity.conf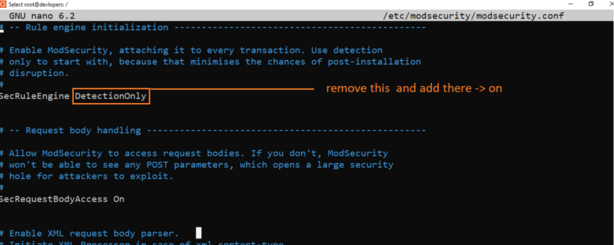
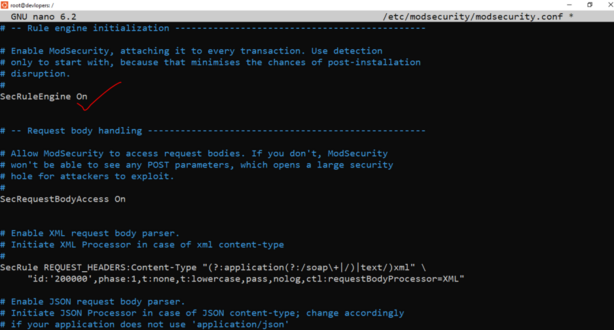
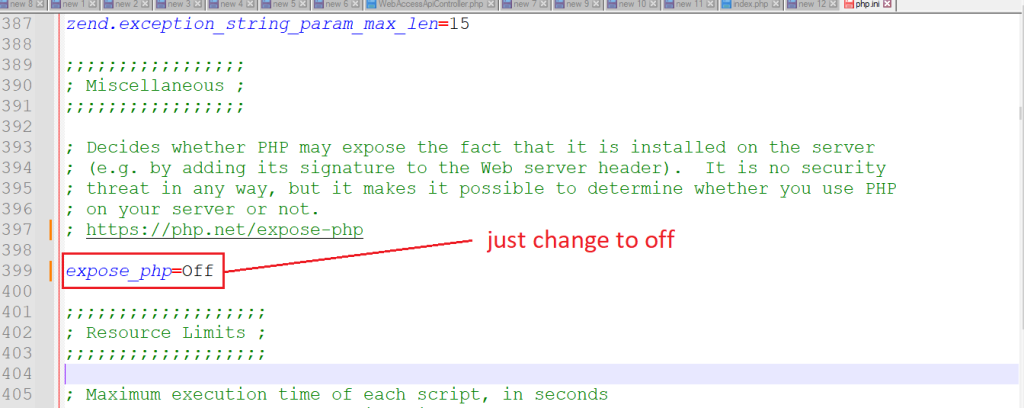
21. Restrict PHP Information Leakage
To restrict PHP information leakage disable expose_php. Edit /etc/php.d/secutity.ini and set the following directive:
expose_php=Off
Example :-
Go to php.ini and disable
Thanks for learning … 👍👍