What is Apache ?
Apache, in the context of web hosting and server software, usually refers to the Apache HTTP Server. Apache is designed to run on various operating systems, including Linux, Unix, Windows, and macOS. This cross-platform compatibility makes it a versatile choice for different environments.
Why We need to do Apache ?
Apache serves as a web server, allowing you to host and deliver web content to users. It handles incoming HTTP requests and serves HTML pages, images, scripts, and other files to clients (web browsers).
Security thread if i ignore Apache
Ignoring security measures for Apache or any web server can expose your system to various threats and vulnerabilities. Here are some potential security risks if you neglect Apache security:
- Unauthorized Access: Without proper access controls, attackers may gain unauthorized access to sensitive files and directories on your web server. This could lead to data breaches or unauthorized modifications.
- Injection Attacks: Ignoring input validation and sanitization can make your web applications susceptible to injection attacks, such as SQL injection or Cross-Site Scripting (XSS), where malicious code is injected into user inputs.
- Denial of Service (DoS) Attacks: Neglecting measures to mitigate DoS attacks can result in your server becoming overwhelmed with traffic, making it unresponsive or causing service degradation.
- Information Disclosure: If server information is not properly restricted, attackers may gather information about your server and exploit known vulnerabilities. This could include details about server software versions, operating system details, and more.
- Outdated Software Vulnerabilities: Failing to keep Apache and its associated software up to date increases the risk of exploitation of known vulnerabilities. Regular updates often include security patches to address newly discovered issues.
- Weak Encryption and SSL/TLS Configuration: Inadequate SSL/TLS configuration can lead to vulnerabilities in the encryption of data transmitted between the server and clients. This could expose sensitive information to eavesdropping.
- Insecure File Permissions: Incorrect file and directory permissions may allow unauthorized users to read, write, or execute files on the server, leading to potential security breaches.
- Lack of Web Application Firewall (WAF): Without a WAF or similar security mechanisms, your web applications are more susceptible to various attacks. A WAF can help protect against common web application vulnerabilities.
- Ignoring Security Headers: Security headers play a crucial role in enhancing the security of your web applications. Neglecting to implement headers like Content Security Policy (CSP) and X-Frame-Options can expose your applications to various threats.
sudo apt update && sudo apt upgrade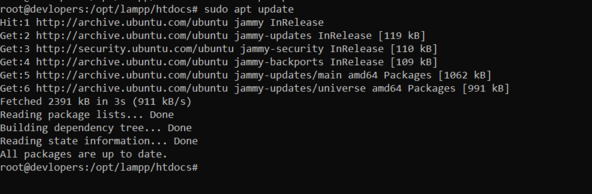
2. Use a strong password for the root user
What is Passowrd for root user ?
Ensure that all user accounts and passwords associated with your Apache server have strong, unique passwords. This helps to prevent brute-force attacks. Instead, it uses a mechanism called sudo to allow authorized users to execute administrative commands.
Why We need to do this root user ?
Setting a root password for the root user in Ubuntu is not a common practice and is generally discouraged. Instead, Ubuntu encourages the use of sudo, a mechanism that allows authorized users to execute administrative commands with their own passwords.
If you ignore setting a root password for a user and rely on the default sudo configuration in Ubuntu, there are some potential security risks and considerations:
- Unauthorized Access: Without a root password, any compromise of the user’s account with sudo privileges would potentially grant an attacker elevated privileges on the system.
- Brute Force Attacks: Without a root password, the root account is more resistant to brute force attacks since attackers cannot directly target the root password. However, it doesn’t eliminate the risk entirely, as attackers might focus on compromising user accounts with sudo access.
- Misuse of Sudo Privileges: Users with sudo access can execute commands with elevated privileges. If their accounts are compromised, an attacker could misuse these privileges to modify system files, install malicious software, or perform other malicious actions.
- Lack of Two-Factor Authentication (2FA) for Sudo: The default sudo configuration in Ubuntu typically relies on the user’s password for authentication. Adding two-factor authentication (2FA) for sudo could enhance security by requiring an additional factor for authorization.
Security thread if i ignore root passowrd for User
If you ignore setting a root password for a user and rely on the default sudo configuration in Ubuntu, there are some potential security risks and considerations:
- Logging and Auditing: While sudo commands are logged, if users are sharing accounts or using a generic sudo user, it might be challenging to attribute specific actions to individual users. This can impact auditing and accountability.
- Security Updates and Patching: Regularly updating the system, including the sudo package, is crucial. Security updates often include fixes for vulnerabilities. Ignoring updates could expose the system to known security issues.
- If multiple users share the same account with sudo privileges, any compromise of that account affects all users sharing it. It’s generally recommended to have individual accounts for each user with sudo access.
Example
sudo passwd root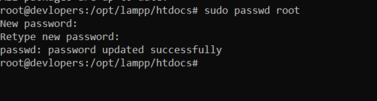
3. “Server Capacity Planning and Dedicated Resource Allocation for Application Server”
Make sure that the server where the application server is installed has the appropriate capacity to handle the load and is not shared with other systems.
- Assess the load requirements of the application server. This includes estimating the number of concurrent users, the number of transactions per second, and the amount of data being processed.
- Identify the resources required by the application server. This includes the CPU, memory, storage, and network bandwidth requirements.
- Select a server that has the appropriate capacity to meet the requirements of the application server. This means selecting a server with the right amount of CPU cores, memory, storage, and network bandwidth.
- Avoid sharing the server with other systems. This is because sharing the server can reduce the resources available to the application server and impact its performance.
4. Enable compression
Enabling compression in Apache can significantly reduce the size of data transferred between the server and clients, leading to faster page load times. The most common method for achieving compression in Apache is by using the mod_deflate module. Here’s how you can enable compression with examples:
Example :-
sudo a2enmod deflateFor RHEL/CentOS systems, you can open Apache configuration file at /etc/httpd/conf/httpd.conf
sudo vi /etc/httpd/conf/httpd.confand uncomment the following line by removing # at the beginning.
LoadModule deflate_module modules/mod_deflate.so
If you don’t find the above line, just add it.
5. Enable GZIP compression in .htaccess
If you have setup Apache Virtual Host, you can open the .htaccess file for your website and add the following lines in it. Else you can create a blank .htaccess file under main document root (/var/www/html)
sudo vim /var/www/html/.htaccessAdd the following lines to it
# GZIP compression for text files: HTML, CSS, JS, Text, XML, fonts
<IfModule mod_deflate.c>
AddOutputFilterByType DEFLATE application/javascript
AddOutputFilterByType DEFLATE application/rss+xml
AddOutputFilterByType DEFLATE application/vnd.ms-fontobject
AddOutputFilterByType DEFLATE application/x-font
AddOutputFilterByType DEFLATE application/x-font-opentype
AddOutputFilterByType DEFLATE application/x-font-otf
AddOutputFilterByType DEFLATE application/x-font-truetype
AddOutputFilterByType DEFLATE application/x-font-ttf
AddOutputFilterByType DEFLATE application/x-javascript
AddOutputFilterByType DEFLATE application/xhtml+xml
AddOutputFilterByType DEFLATE application/xml
AddOutputFilterByType DEFLATE font/opentype
AddOutputFilterByType DEFLATE font/otf
AddOutputFilterByType DEFLATE font/ttf
AddOutputFilterByType DEFLATE image/svg+xml
AddOutputFilterByType DEFLATE image/x-icon
AddOutputFilterByType DEFLATE text/css
AddOutputFilterByType DEFLATE text/html
AddOutputFilterByType DEFLATE text/javascript
AddOutputFilterByType DEFLATE text/plain
AddOutputFilterByType DEFLATE text/xml
</IfModule>What are the Benefits of using Enable Compression
- Reduced bandwidth usage: GZIP compression can reduce the size of HTTP responses by up to 90%, which can significantly reduce bandwidth usage. This can be especially beneficial for websites with a lot of text-based content, such as blogs and news websites.
- Improved performance: By reducing the size of HTTP responses, GZIP compression can also improve the performance of your website by reducing the time it takes for pages to load. This is because the browser will be able to download the smaller responses more quickly.
We use AddOutputFilterByType directive to tell Apache as to which file types to compress.
Next restart the apache server
sudo /opt/lampp/lampp restart6. Tune the MPM
What is Tune the MPM ?
Tuning the MPM (Multi-Processing Module) in Apache refers to optimizing the configuration settings of the MPM module to achieve better performance and resource utilization. The MPM is responsible for handling incoming requests by creating and managing worker processes or threads. Apache supports different MPMs, and the most commonly used ones are prefork, worker, and event.
Here are some key considerations for tuning the Apache MPM:
1. Choose the Right MPM:
- Apache provides different MPMs, and the choice depends on the requirements of your application. Common MPMs include:
prefork: Suitable for non-thread-safe applications, such as those using mod_php.worker: Combines multiple processes with multiple threads per process.event: Similar toworkerbut with improvements for handling keep-alive connections.
The MPM module that you select will determine how Apache handles requests and how it scales to handle more traffic.
Example :-
7. KeepAlive
KeepAlive is an Apache directive that allows Apache to keep connections open for multiple requests. This can improve performance by reducing the number of times that Apache needs to create and destroy connections.
Benefits of using KeepAlive
There are several benefits to using KeepAlive in Apache:
- Reduced connection overhead: KeepAlive can reduce the amount of overhead associated with creating and destroying connections. This can improve performance by reducing the amount of time that Apache needs to spend on connection management.
- Improved performance for multiple requests: KeepAlive can improve the performance of websites that require multiple requests to be processed, such as websites that use JavaScript frameworks.
- Reduced resource usage: KeepAlive can reduce the amount of resources that Apache needs to use, such as CPU and memory.
Example :-
It is simple to do so by making the following changes to the httpd.conf configuration file for Apache:
- KeepAlive: Set it to “KeepAlive on” to enable Keep-Alive. To disable it, use “KeepAlive off”.
KeepAlive On
MaxKeepAliveRequests 100
KeepAliveTimeout 158.Implement IP Blacklisting (Fail2Ban):
What is Fail2Ban ?
Fail2Ban is a security tool commonly used on Unix-like systems, including Ubuntu, to protect against unauthorized access attempts by monitoring and responding to suspicious activities. Its primary purpose is to identify and block malicious users or bots that may be attempting to exploit vulnerabilities in services like SSH, Apache, Nginx, or others.
Why We need to do this Fail2Ban ?
Fail2Ban is a valuable security tool for several reasons, and its use is recommended for enhancing the security of systems, especially those exposed to the internet. Here are key reasons why using Fail2Ban is beneficial:
- Mitigating Brute-Force Attacks:
- SSH Protection: Fail2Ban protects against brute-force attacks on services like SSH by dynamically blocking IP addresses that repeatedly fail authentication attempts. This helps prevent unauthorized access.
- Enhancing System Security:
- Web Server Protection: For web servers (e.g., Apache or Nginx), Fail2Ban helps protect against malicious activities, such as attempts to exploit vulnerabilities or conduct brute-force attacks on login pages.
- Dynamic Response to Threats:
- Automatic Blocking: Fail2Ban dynamically adjusts firewall rules to block IP addresses exhibiting suspicious behavior. This automated response helps in real-time defense against emerging threats.
- Reducing Attack Surface:
- Temporary Blocks: Fail2Ban imposes temporary bans, reducing the window of opportunity for attackers. This approach minimizes the impact on legitimate users and services.
Security thread if i ignore Fail2Ban
Ignoring Fail2Ban or not implementing similar security measures leaves your system vulnerable to several security threats, especially those related to brute-force attacks and unauthorized access attempts. Here are the potential security threats and risks associated with not using Fail2Ban:
- Brute-Force Attacks:
- Increased Vulnerability: Without Fail2Ban, your system becomes more susceptible to brute-force attacks, where attackers systematically attempt to gain access by trying different username and password combinations.
- Credential Compromise: Successful brute-force attacks can lead to the compromise of user accounts, potentially exposing sensitive data or allowing unauthorized system access.
- Unauthorized Access:
- Account Takeover: Lack of protection against multiple failed login attempts increases the risk of unauthorized access to user accounts, including administrator accounts.
- Malicious Activities: Attackers gaining unauthorized access can engage in malicious activities, such as data theft, system manipulation, or the installation of malware.
- Resource Exhaustion:
- CPU and Network Resource Drain: Brute-force attacks can lead to resource exhaustion, causing excessive CPU and network bandwidth usage. This can impact the performance of the system and other services.
- Increased Attack Surface:
- Expanded Window of Opportunity: Failing to implement dynamic blocking mechanisms means that attackers have a longer window of opportunity to carry out brute-force attacks without facing consequences.
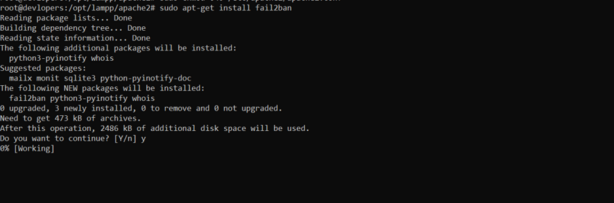
9. Never Keep Unused Modules
Security risk
Unused modules can be a security risk because they can provide potential attackers with additional entry points to your server. Attackers can exploit vulnerabilities in unused modules to gain access to your server and steal data or launch attacks against other systems.
Performance impact
Unused modules can also impact performance because they consume resources that could otherwise be used by Apache to process requests. Even if an unused module is not actively processing requests, it can still consume resources by running in the background or by registering hooks with Apache.
10. Use Content Delivery Networks
Content Delivery Networks (CDNs) are a network of servers distributed around the world that deliver content to users based on their geographic location. This can improve performance by reducing the distance that data has to travel and by offloading some of the load from your Apache server.
To use a CDN with Apache, you need to create an account with a CDN provider and configure your Apache server to serve content from the CDN.
Here’s an example Apache virtual host configuration
<VirtualHost *:80>
ServerName yourdomain.com
DocumentRoot /var/www/html
# CDN Rewriting
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTP:X-Forwarded-Proto} !https
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
</IfModule>
# Other Apache Configuration Directives...
</VirtualHost>

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687 |
+91 8409492687 |  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
[…] List of Performance Checklist for Apache […]