What is fail2ban ?
Fail2Ban is like a bouncer for your server. It’s a security tool that helps protect your system from brute-force attacks by monitoring log files for malicious activity. When it detects multiple failed login attempts or other suspicious behavior from an IP address, it dynamically updates firewall rules to block that address and prevent further access.
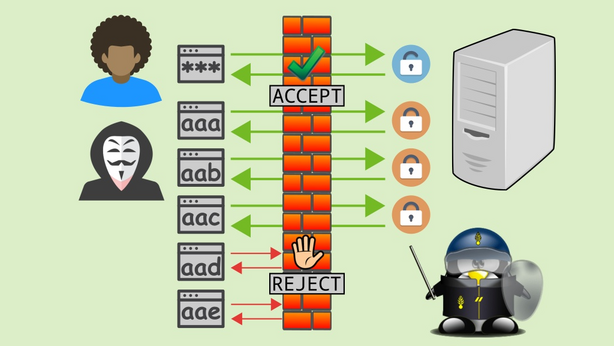
Security thread using of fail2ban
Fail2ban is a powerful tool that can be used to protect Linux servers from a variety of attacks. Here are some of the benefits of using Fail2ban:
- Improved security: Fail2ban can help to improve the security of your Linux server by blocking malicious IP addresses. This can help to protect your server from brute-force login attempts, denial-of-service (DoS) attacks, and port scans.
- Reduced load on your server: Fail2ban can help to reduce the load on your server by blocking malicious traffic. This can improve the performance of your server and make it less vulnerable to attack.
- Compliance: Fail2ban can help you to comply with a variety of security regulations, such as PCI DSS and HIPAA.
- Easy to use: Fail2ban is a relatively easy to use tool. It can be installed and configured with a few simple commands.
- Flexible: Fail2ban is a flexible tool. It can be configured to meet the specific needs of your server.
Insallation process
sudo apt-get install fail2ban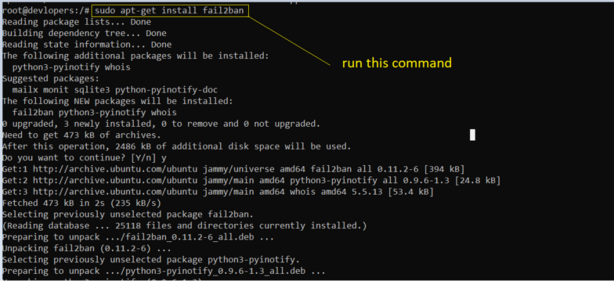
2nd step go to below path and add below code
cd /etc/fail2ban[sshd]
enabled = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3
findtime = 300
bantime = 86400
ignoreip = 127.0.0.1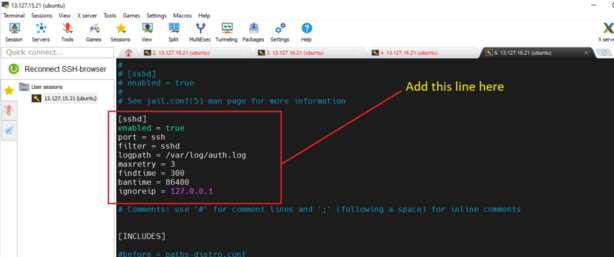
After adding save and exit.
Restart the server
sudo systemctl restart fail2ban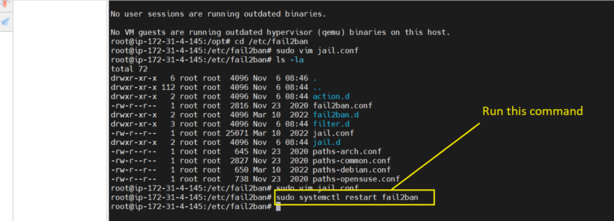
Once Fail2ban is enabled and running, it will start monitoring the SSH service for malicious activity. If Fail2ban detects malicious activity, it will ban the IP address that is responsible for the activity.
Thanks for learning 👍👍