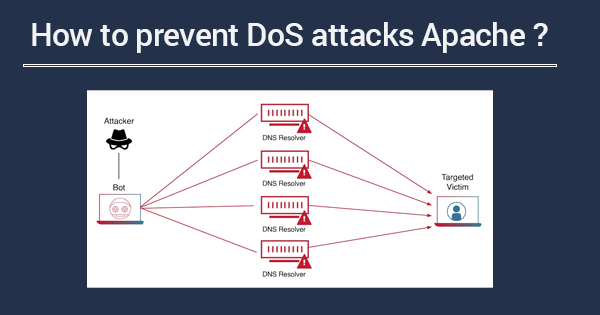
Preventing Denial of Service (DoS) attacks against Apache involves implementing various security measures to mitigate the impact of such attacks. While it’s challenging to entirely prevent all types of DoS attacks, you can take steps to minimize their impact. Here are some practical Linux security measures along with example commands for Apache:
1. Install and Configure ModSecurity:
ModSecurity is an open-source web application firewall (WAF) engine for Apache, IIS, and Nginx. It is used to protect web applications from a wide range of attacks, including:
- SQL injection
- Cross-site scripting (XSS)
- Local file inclusion (LFI)
- Remote code execution (RCE)
- Denial-of-service (DoS) attacks
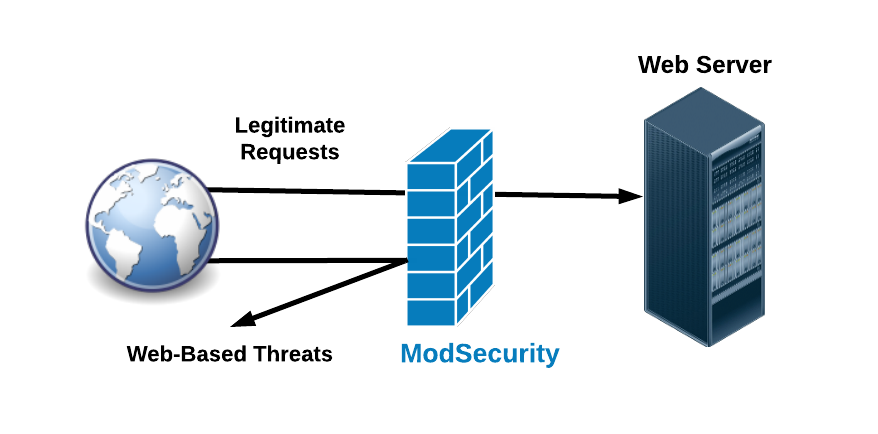
ModSecurity can be configured to block attacks, log suspicious activity, or both. It can also be used to implement security policies, such as limiting the number of concurrent requests from a single IP address.
To install ModSecurity on Linux, you can use the following steps:
- Install the ModSecurity package for your Linux distribution.
- Configure ModSecurity. You can do this by editing the ModSecurity configuration file, which is typically located at
/etc/modsecurity/modsecurity.conf.
sudo apt install libapache2-mod-security2
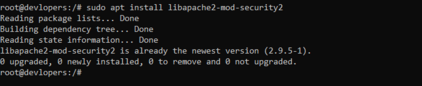
2nd step run below code
sudo a2enmod security2
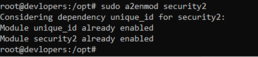
3rd step
nano /etc/apache2/mods-enabled/security2.conf
<IfModule security2_module>
# Default Debian dir for modsecurity's persistent data
SecDataDir /var/cache/modsecurity
# Include all the *.conf files in /etc/modsecurity.
# Keeping your local configuration in that directory
# will allow for an easy upgrade of THIS file and
# make your life easier
IncludeOptional /etc/modsecurity/*.conf
# Include OWASP ModSecurity CRS rules if installed
IncludeOptional /usr/share/modsecurity-crs/*.load
</IfModule>
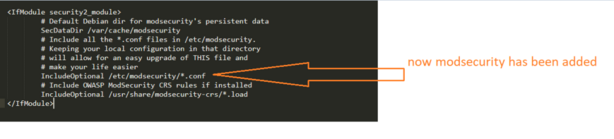
4th step
sudo mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
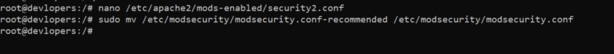
5th step
sudo nano /etc/modsecurity/modsecurity.conf
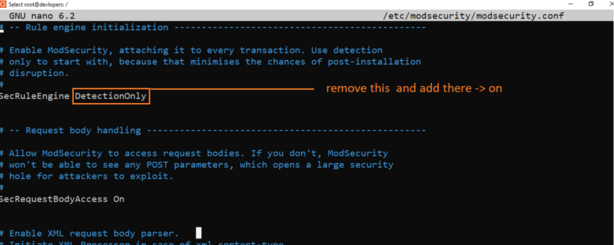
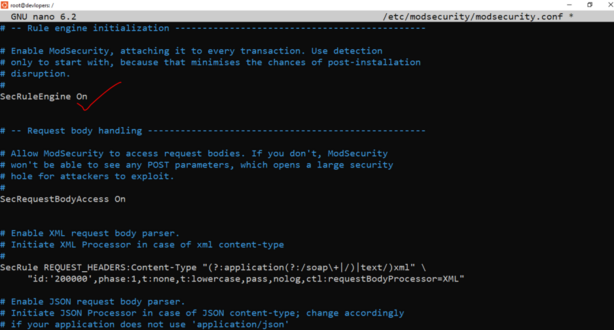
Type below code
ABCEFHJKZ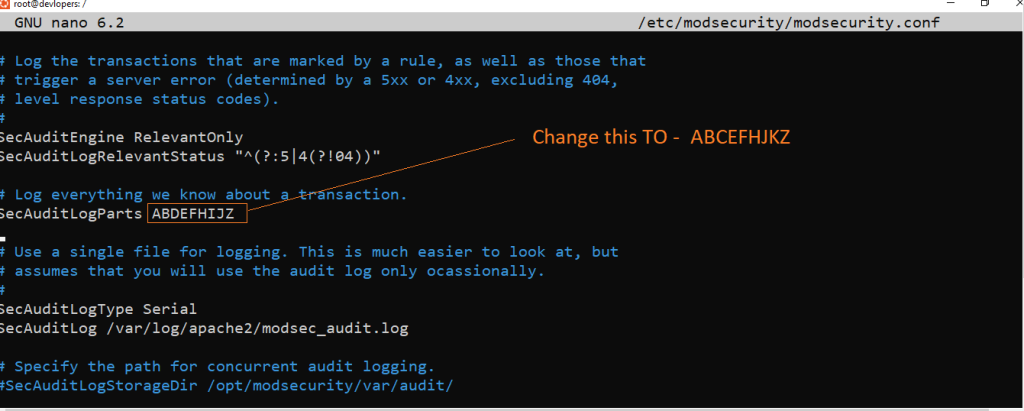
Now all configuration setup successfully…
- Web Application Firewall (WAF):
- Implement a Web Application Firewall like ModSecurity with appropriate rule sets (e.g., OWASP Core Rule Set).
- IP Whitelisting and Blacklisting:
- Use Apache
allowanddenydirectives to whitelist trusted IP addresses and block malicious ones.
- Use Apache
- Load Balancing and Failover:
- Distribute traffic across multiple servers using load balancing.
- Implement failover mechanisms to switch to backup servers if an attack is detected.
- Cloud-Based DDoS Protection:
- Consider using cloud-based DDoS protection services such as Cloudflare or Akamai.
- Monitoring and Logging:
- Regularly monitor Apache logs for unusual patterns or spikes in traffic.
- Set up alerting mechanisms to notify administrators of potential attacks.
- Implement Connection Limits:
- Use Apache directives like
MaxClients,MaxRequestsPerChild, andMaxConnectionsPerChildto control the number of connections.
- Use Apache directives like
- Update and Patch:
- Keep Apache and related software up to date with the latest security patches.
- Educate Users:
- Train users and administrators on recognizing and reporting potential DoS attacks.
- Firewall Configuration:
- Use server-level firewalls or external firewalls to filter and control incoming traffic.
Always tailor these measures to your specific environment, and regularly review and update your security measures to adapt to evolving threats. Testing in a controlled environment is crucial before applying changes to production.