In this tutorial we’re going to learn top 21 security checklist for Apache Configuration. Apache web server is crucial to safeguarding your website and its data. This tutorial provides a comprehensive 30-step checklist with practical examples to enhance the security of your Apache server.
1. Keep Apache up to date
It’s always recommended to keep all your applications up to date, as the latest applications come with bug fixes and security patches that address underlying vulnerabilities present in older software versions.
What is Apache ?
Apache, in the context of web hosting and server software, usually refers to the Apache HTTP Server. Apache is designed to run on various operating systems, including Linux, Unix, Windows, and macOS. This cross-platform compatibility makes it a versatile choice for different environments.
Why We need to do Apache ?
Apache serves as a web server, allowing you to host and deliver web content to users. It handles incoming HTTP requests and serves HTML pages, images, scripts, and other files to clients (web browsers).
Security thread if i ignore Apache
Ignoring security measures for Apache or any web server can expose your system to various threats and vulnerabilities. Here are some potential security risks if you neglect Apache security:
- Unauthorized Access: Without proper access controls, attackers may gain unauthorized access to sensitive files and directories on your web server. This could lead to data breaches or unauthorized modifications.
- Injection Attacks: Ignoring input validation and sanitization can make your web applications susceptible to injection attacks, such as SQL injection or Cross-Site Scripting (XSS), where malicious code is injected into user inputs.
- Denial of Service (DoS) Attacks: Neglecting measures to mitigate DoS attacks can result in your server becoming overwhelmed with traffic, making it unresponsive or causing service degradation.
- Information Disclosure: If server information is not properly restricted, attackers may gather information about your server and exploit known vulnerabilities. This could include details about server software versions, operating system details, and more.
- Outdated Software Vulnerabilities: Failing to keep Apache and its associated software up to date increases the risk of exploitation of known vulnerabilities. Regular updates often include security patches to address newly discovered issues.
- Weak Encryption and SSL/TLS Configuration: Inadequate SSL/TLS configuration can lead to vulnerabilities in the encryption of data transmitted between the server and clients. This could expose sensitive information to eavesdropping.
- Insecure File Permissions: Incorrect file and directory permissions may allow unauthorized users to read, write, or execute files on the server, leading to potential security breaches.
- Lack of Web Application Firewall (WAF): Without a WAF or similar security mechanisms, your web applications are more susceptible to various attacks. A WAF can help protect against common web application vulnerabilities.
- Ignoring Security Headers: Security headers play a crucial role in enhancing the security of your web applications. Neglecting to implement headers like Content Security Policy (CSP) and X-Frame-Options can expose your applications to various threats.
sudo apt update && sudo apt upgrade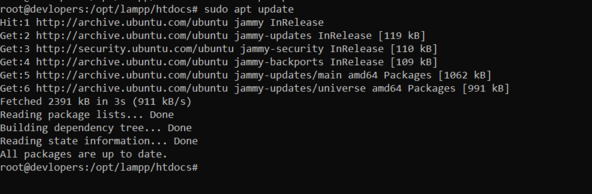
2. Use a strong password for the root user
What is Passowrd for root user ?
Ensure that all user accounts and passwords associated with your Apache server have strong, unique passwords. This helps to prevent brute-force attacks. Instead, it uses a mechanism called sudo to allow authorized users to execute administrative commands.
Why We need to do this root user ?
Setting a root password for the root user in Ubuntu is not a common practice and is generally discouraged. Instead, Ubuntu encourages the use of sudo, a mechanism that allows authorized users to execute administrative commands with their own passwords.
If you ignore setting a root password for a user and rely on the default sudo configuration in Ubuntu, there are some potential security risks and considerations:
- Unauthorized Access: Without a root password, any compromise of the user’s account with sudo privileges would potentially grant an attacker elevated privileges on the system.
- Brute Force Attacks: Without a root password, the root account is more resistant to brute force attacks since attackers cannot directly target the root password. However, it doesn’t eliminate the risk entirely, as attackers might focus on compromising user accounts with sudo access.
- Misuse of Sudo Privileges: Users with sudo access can execute commands with elevated privileges. If their accounts are compromised, an attacker could misuse these privileges to modify system files, install malicious software, or perform other malicious actions.
- Lack of Two-Factor Authentication (2FA) for Sudo: The default sudo configuration in Ubuntu typically relies on the user’s password for authentication. Adding two-factor authentication (2FA) for sudo could enhance security by requiring an additional factor for authorization.
Security thread if i ignore root passowrd for User
If you ignore setting a root password for a user and rely on the default sudo configuration in Ubuntu, there are some potential security risks and considerations:
- Logging and Auditing: While sudo commands are logged, if users are sharing accounts or using a generic sudo user, it might be challenging to attribute specific actions to individual users. This can impact auditing and accountability.
- Security Updates and Patching: Regularly updating the system, including the sudo package, is crucial. Security updates often include fixes for vulnerabilities. Ignoring updates could expose the system to known security issues.
- If multiple users share the same account with sudo privileges, any compromise of that account affects all users sharing it. It’s generally recommended to have individual accounts for each user with sudo access.
Example
sudo passwd root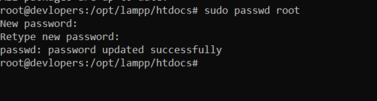
3. Add an SSL Certificate
An SSL certificate is a digital certificate that authenticates a website’s identity and enables an encrypted connection. SSL stands for Secure Sockets Layer, a security protocol that creates an encrypted link between a web server and a web browser.
What is SSL Certificate ?
SSL (Secure Sockets Layer) certificate is a digital certificate that provides a secure and encrypted connection between a web server and a web browser. The SSL/TLS protocols encrypt the data transmitted between the server and the browser, ensuring the confidentiality and integrity of the information exchanged.
Why We need to do SSL Certificate?
Implementing an SSL (Secure Sockets Layer) certificate for your website offers several important benefits, contributing to both security and user experience. Here are compelling reasons to use an SSL certificate:
- Data Encryption: SSL certificates encrypt the data transmitted between a user’s browser and your website’s server. This encryption ensures that sensitive information, such as login credentials, personal details, and financial transactions, remains confidential and secure.
- User Privacy and Trust: SSL establishes a secure and private connection, building trust with your website visitors. Users are more likely to share personal information and engage with your site if they see the padlock icon and “https://” in the address bar, indicating a secure connection.
- Authentication: SSL certificates authenticate the identity of your website, assuring users that they are connecting to the legitimate and intended site. This helps prevent phishing attacks and builds credibility.
- Protection Against Man-in-the-Middle Attacks: SSL protects against man-in-the-middle attacks where an attacker intercepts and manipulates the communication between a user and a website. With encryption, it becomes significantly more difficult for attackers to eavesdrop on or alter the data being transmitted.
Security thread if i ignore SSL Certificate
Ignoring the implementation of an SSL (Secure Sockets Layer) certificate for your website exposes it to various security threats and risks. Here are some security threats associated with not using an SSL certificate:
- Data Interception: Without SSL encryption, data transmitted between a user’s browser and the server is vulnerable to interception by malicious actors. This can lead to the exposure of sensitive information such as login credentials, personal details, and financial data.
- Man-in-the-Middle Attacks: In the absence of SSL, attackers can carry out man-in-the-middle attacks, intercepting and manipulating the communication between the user and the website. This can result in unauthorized access, data tampering, and the injection of malicious content.
- Privacy Concerns: Users are increasingly concerned about privacy, and without SSL, your website may be perceived as insecure. Users may be hesitant to share personal information, reducing engagement and trust in your site.
- Phishing Risks: Websites without SSL are more susceptible to phishing attacks. Attackers can create fraudulent sites that mimic yours, tricking users into entering sensitive information on these fake sites.
SSL installation example :-
sudo apt install certbot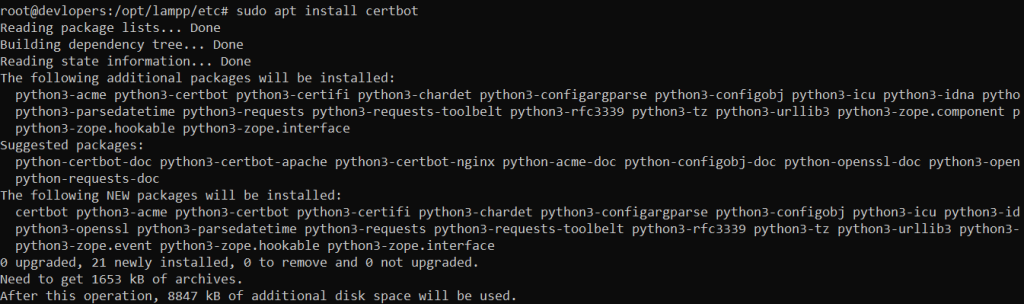
4.Use a SQL injection filter
What is Mod-security2 ?
ModSecurity, often referred to as mod_security or mod_security2, is an open-source web application firewall (WAF) module that is typically deployed with the Apache HTTP Server. It provides a set of tools for monitoring and securing web applications by applying various security rules and policies.
Why We need to do this Mod-security2 ?
Implementing ModSecurity, or ModSecurity2, is beneficial for several reasons, especially when it comes to enhancing the security posture of web applications and protecting against various cyber threats. Here are some key reasons why organizations use ModSecurity:
- Protection Against Web Application Attacks: ModSecurity acts as a web application firewall (WAF), providing protection against a wide range of web application attacks, including SQL injection, cross-site scripting (XSS), and other common vulnerabilities. It helps to filter malicious traffic before it reaches the web application.
- Prevention of SQL Injection and Cross-Site Scripting: SQL injection and XSS are common attack vectors where attackers attempt to inject malicious code into web applications. ModSecurity can detect and prevent these types of attacks by analyzing and filtering incoming requests.
- Security Compliance: Many regulatory standards and security best practices recommend or require the implementation of a WAF for web applications. ModSecurity helps organizations achieve and maintain compliance with standards such as PCI DSS (Payment Card Industry Data Security Standard) and others.
- Real-time Monitoring and Incident Response: ModSecurity provides real-time monitoring of web traffic and logs security events. This allows security teams to analyze and respond to incidents promptly. The detailed logging helps in identifying the nature of attacks and understanding the security posture of the web application.
Security thread if i ignore Mod-security2
If your’re Ignoring ModSecurity2 then your web applications vulnerable to a range of security threats. Here are some potential security threats and risks associated with not using ModSecurity2:
- SQL Injection Attacks: Without a WAF like ModSecurity, your web applications may be susceptible to SQL injection attacks. Attackers can inject malicious SQL queries into input fields, potentially leading to unauthorized access, data manipulation, or data theft.
- Cross-Site Scripting (XSS) Attacks: XSS attacks involve injecting malicious scripts into web pages viewed by other users. Without protection, your applications may be vulnerable to these attacks, which can lead to session hijacking, defacement, or the theft of sensitive information.
- Cross-Site Request Forgery (CSRF) Attacks: CSRF attacks involve tricking a user’s browser into making unintended requests. ModSecurity can help detect and prevent these attacks by validating and blocking malicious requests.
- Security Compliance Violations: Many regulatory standards and compliance requirements mandate the use of a web application firewall. Ignoring ModSecurity may lead to non-compliance with standards such as PCI DSS, exposing your organization to potential legal and financial consequences.
Installation of ModSecurity:
sudo apt install libapache2-mod-security2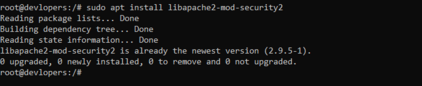
Run below code
sudo a2enmod security2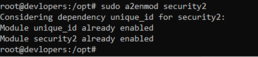
nano /etc/apache2/mods-enabled/security2.conf<IfModule security2_module>
# Default Debian dir for modsecurity's persistent data
SecDataDir /var/cache/modsecurity
# Include all the *.conf files in /etc/modsecurity.
# Keeping your local configuration in that directory
# will allow for an easy upgrade of THIS file and
# make your life easier
IncludeOptional /etc/modsecurity/*.conf
# Include OWASP ModSecurity CRS rules if installed
IncludeOptional /usr/share/modsecurity-crs/*.load
</IfModule>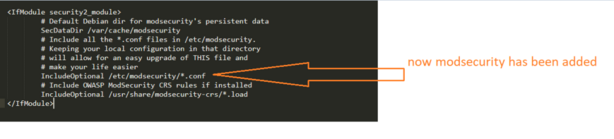
sudo mv /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
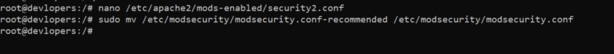
sudo nano /etc/modsecurity/modsecurity.conf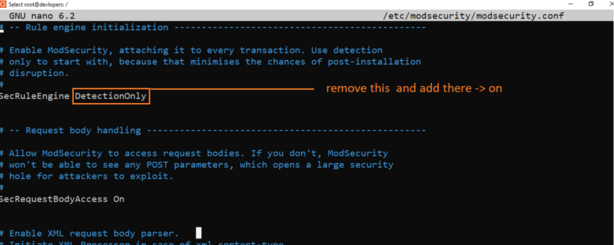
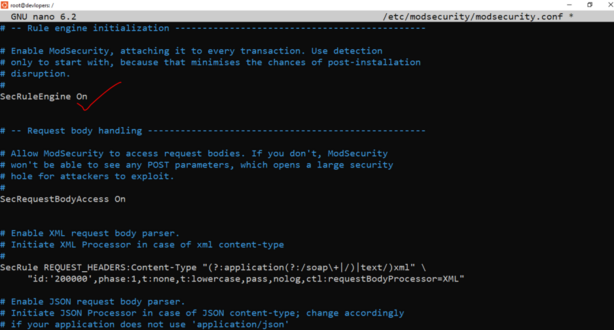
Type below code
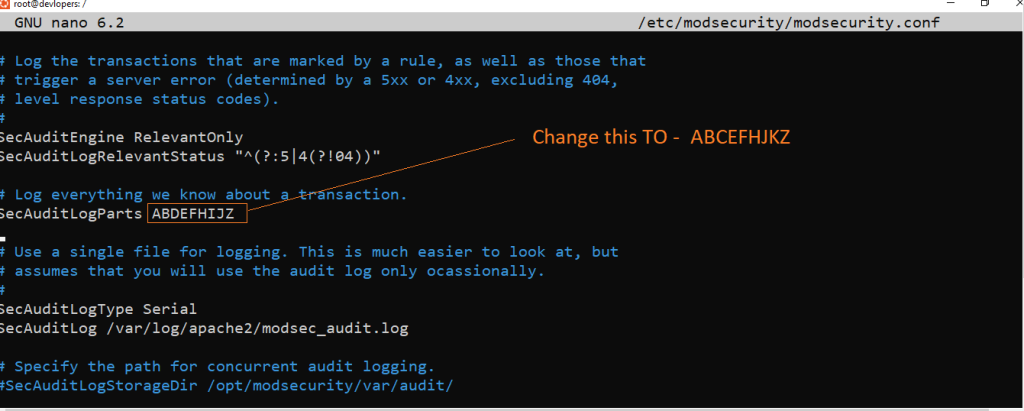
5. Disable Directory Listing
What is Directory Listing ?
Directory listing, also known as directory listing or directory browsing, is the process of displaying the contents of a directory (folder) when there is no default index file (e.g., index.html) present in that directory. This means that if someone accesses a directory on a web server, and there is no default index file, the server may show a list of files and subdirectories within that directory.
Why We need to do Disable Directory Listing ?
Disabling directory listing in Apache is a security best practice for several reasons:
- Information Disclosure:
- Risk: Directory listing exposes the contents of directories, revealing file and directory names.
- Impact: Attackers can gather information about the server’s directory structure, potentially identifying sensitive files or locations.
- Security Through Obscurity:
- Risk: Relying on security through obscurity (hiding information) is not a recommended practice.
- Impact: Directory listing provides unnecessary information to potential attackers, increasing the attack surface.
- Privacy and Compliance:
- Risk: Exposing directory contents may violate privacy or compliance regulations.
- Impact: Compliance with privacy laws and regulations may be compromised by revealing directory information.
- Preventing Enumeration Attacks:
- Risk: Directory listing facilitates enumeration attacks where attackers systematically discover directories and files.
- Impact: Attackers can gather intelligence about the server environment, aiding in planning more targeted attacks.
Security thread if i ignore Disable Directory Listing?
If you ignore to disable directory listing, you are leaving yourself open to a number of security threats, including:
- Information disclosure: Attackers can use directory listing to identify sensitive files and directories on your web server. This information can then be used to target the web server with more specific attacks.
- Denial-of-service attacks: Attackers can use directory listing to consume all of the available bandwidth on your web server. This would prevent legitimate users from being able to access the web server.
- Malware injection: Attackers can use directory listing to identify files that are vulnerable to malware injection. They can then exploit these vulnerabilities to inject malicious code into the files. This malicious code could then be executed when the files are accessed by legitimate users.
Example :-
Go to .htaccess file in the directory where you want to disable directory listing.
- Open the .htaccess file in a text editor.
- Add the following line to the file:
Options -IndexesSave the .htaccess file.
6. Disable .htaccess Override
What is .htaccess ?
.htaccess files (or “distributed configuration files”) provide a way to make configuration changes on a per-directory basis. A file, containing one or more configuration directives, is placed in a particular document directory, and the directives apply to that directory and all subdirectories thereof.
If you have access to the httpd main server config file, you should avoid using .htaccess files entirely. The use of .htaccess files causes your Apache HTTP server to slow down. Any directive included in a.htaccess file is preferably placed in a Directory block since it will have the same impact while performing better.
Why need to do .htaccess ?
The .htaccess file is a powerful and flexible configuration file used by Apache web servers. Here are some common reasons why you might need to use .htaccess:
- Per-Directory Configuration:
.htaccessallows you to configure settings on a per-directory basis. This is particularly useful when you don’t have access to the main server configuration file, such as in shared hosting environments. - URL Rewriting:
.htaccessis commonly used for URL rewriting. You can use mod_rewrite rules to create search engine-friendly URLs, redirect URLs, or rewrite URLs to point to different resources on your server. - Password Protection: You can use
.htaccessto set up password protection for specific directories. This is achieved through theAuthTypeandAuthUserFiledirectives.
Security thread if i ignore this .htaccess ?
Ignoring the use of .htaccess can introduce security risks and limit your ability to implement certain security measures. Here are some potential security threats and considerations if you choose to ignore or avoid using .htaccess:
- URL Rewriting Security: Without the ability to use
.htaccessfor URL rewriting, you might miss out on implementing secure URL structures or fail to properly handle redirects. This could impact SEO and user experience. - Password Protection: If you don’t use
.htaccessfor password protection, sensitive directories might be accessible to unauthorized users. This is crucial for protecting sensitive areas of your website. - Custom Error Pages: Without custom error pages in
.htaccess, your website might display generic error messages, potentially revealing sensitive information about your server or application. - Redirect Security: Lack of proper redirection management might expose users to phishing attempts or incorrect URLs. Properly managed redirects help ensure users are directed to the correct and secure locations.
- Security Headers: Security headers, such as Content Security Policy (CSP), can be configured in
.htaccessto enhance the security of your web application. Ignoring this might leave your website more vulnerable to certain types of attacks.
Example:-
<Directory "/path/to/your/directory">
AllowOverride None
# other directory configurations...
</Directory>7. Enable Firewall and Allow Necessary Ports:
What is Firewall and Allow Necessary Ports ?
Enabling a firewall and allowing necessary ports are security measures to control and regulate network traffic to and from your computer or server. Firewalls act as a barrier between your system and the internet or other networks, helping to prevent unauthorized access and securing your system.
Why We need to do this Firewall Ports ?
Enabling a firewall and managing open ports is a crucial aspect of securing your computer or server. Here’s why managing firewall ports is important:
- Security:
- Unauthorized Access Prevention: Firewalls help prevent unauthorized access to your system by blocking incoming connections that are not explicitly allowed.
- Network Segmentation: By controlling which ports are open, you can segment your network and limit exposure to potential security threats.
- Protection Against Exploits:
- Exploit Prevention: Firewalls protect your system from potential exploits and attacks by controlling which services and ports are accessible.
- Controlled Access to Services:
- Service Restriction: You can control which services are accessible from the network. For example, you may allow access to web services (HTTP and HTTPS) but restrict access to certain administrative services.
Security thread if i ignore this Firewall and Allow Necessary Ports ?
If you ignore your firewall and allow necessary ports, you could be putting your system at risk of a number of security threats, including:
- Malware attacks: Malware can exploit open ports to gain access to your system and steal your data, install malware, or launch denial-of-service (DoS) attacks.
- Unauthorized access: Attackers can use open ports to gain unauthorized access to your system and steal your data, or launch attacks against other systems on the network.
- DoS attacks: DoS attacks can overwhelm your system with traffic, making it unavailable to legitimate users.
- Man-in-the-middle attacks: Man-in-the-middle attacks allow attackers to intercept and modify communication between your system and other systems on the network.
Example :-
sudo ufw allow 80
sudo ufw allow 443
sudo ufw enable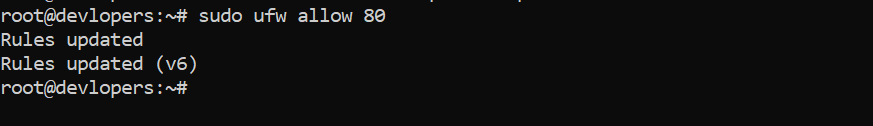
8. Secure File Permissions:
What is the File Permission ?
The permissions of a secure file in Ubuntu will depend on the specific file and its intended use. However, there are some general principles that can be followed:
- The owner of the file should have read and write permissions. This will allow the owner to access and modify the file as needed.
- Other users should have read-only permissions. This will allow other users to view the file, but not modify it.
- The file should not be executable. This will prevent the file from being accidentally or maliciously executed.
Why We need to do this File Permission ?
Setting file permissions is an essential aspect of system security, and it serves several important purposes:
- Access Control:
- User-Level Control: File permissions allow you to control which users or groups have access to a particular file or directory.
- Read, Write, Execute Control: You can specify whether a user has read, write, or execute permissions on a file or directory.
- Security:
- Preventing Unauthorized Access: Properly configured file permissions help prevent unauthorized access to sensitive files or directories.
- Mitigating Exploits: By restricting certain permissions, you can reduce the risk of exploitation by malicious actors.
- Data Integrity:
- Preventing Accidental Modifications: Write permissions control the ability to modify files. By restricting write access, you can prevent accidental changes to critical files.
- Privacy:
- Controlled Sharing: File permissions enable controlled sharing of resources. You can share files with specific users or groups while keeping others out.
- Compliance:
- Meeting Regulatory Requirements: Many industries and organizations have regulatory requirements that mandate strict control over access to certain types of data.
- System Stability:
- Preventing Accidental Deletions: Proper file permissions prevent accidental deletion of critical system files or directories.
Security thread if i ignore permission of secure file in ubuntu
If you ignore the permissions of a secure file in Ubuntu, you could be putting your system at risk of a number of security threats, including:
- Malware attacks: Malware can exploit file permissions to gain access to your system and steal your data, install malware, or launch denial-of-service (DoS) attacks.
- Unauthorized access: Attackers can use file permissions to gain unauthorized access to your system and steal your data, or launch attacks against other systems on the network.
- Data breaches: If a sensitive file is accidentally or maliciously made accessible to unauthorized users, it could lead to a data breach.
- System corruption: If an attacker modifies a system file, it could corrupt the system and make it unusable.
Example:-
chmod 755 filename
9.Implement IP Blacklisting (Fail2Ban):
What is Fail2Ban ?
Fail2Ban is a security tool commonly used on Unix-like systems, including Ubuntu, to protect against unauthorized access attempts by monitoring and responding to suspicious activities. Its primary purpose is to identify and block malicious users or bots that may be attempting to exploit vulnerabilities in services like SSH, Apache, Nginx, or others.
Why We need to do this Fail2Ban ?
Fail2Ban is a valuable security tool for several reasons, and its use is recommended for enhancing the security of systems, especially those exposed to the internet. Here are key reasons why using Fail2Ban is beneficial:
- Mitigating Brute-Force Attacks:
- SSH Protection: Fail2Ban protects against brute-force attacks on services like SSH by dynamically blocking IP addresses that repeatedly fail authentication attempts. This helps prevent unauthorized access.
- Enhancing System Security:
- Web Server Protection: For web servers (e.g., Apache or Nginx), Fail2Ban helps protect against malicious activities, such as attempts to exploit vulnerabilities or conduct brute-force attacks on login pages.
- Dynamic Response to Threats:
- Automatic Blocking: Fail2Ban dynamically adjusts firewall rules to block IP addresses exhibiting suspicious behavior. This automated response helps in real-time defense against emerging threats.
- Reducing Attack Surface:
- Temporary Blocks: Fail2Ban imposes temporary bans, reducing the window of opportunity for attackers. This approach minimizes the impact on legitimate users and services.
Security thread if i ignore Fail2Ban
Ignoring Fail2Ban or not implementing similar security measures leaves your system vulnerable to several security threats, especially those related to brute-force attacks and unauthorized access attempts. Here are the potential security threats and risks associated with not using Fail2Ban:
- Brute-Force Attacks:
- Increased Vulnerability: Without Fail2Ban, your system becomes more susceptible to brute-force attacks, where attackers systematically attempt to gain access by trying different username and password combinations.
- Credential Compromise: Successful brute-force attacks can lead to the compromise of user accounts, potentially exposing sensitive data or allowing unauthorized system access.
- Unauthorized Access:
- Account Takeover: Lack of protection against multiple failed login attempts increases the risk of unauthorized access to user accounts, including administrator accounts.
- Malicious Activities: Attackers gaining unauthorized access can engage in malicious activities, such as data theft, system manipulation, or the installation of malware.
- Resource Exhaustion:
- CPU and Network Resource Drain: Brute-force attacks can lead to resource exhaustion, causing excessive CPU and network bandwidth usage. This can impact the performance of the system and other services.
- Increased Attack Surface:
- Expanded Window of Opportunity: Failing to implement dynamic blocking mechanisms means that attackers have a longer window of opportunity to carry out brute-force attacks without facing consequences.
10 Use a security scanner to scan your web applications for vulnerabilities.
what is nikto ?
Nikto is an open-source web server scanner that is widely used for identifying potential security vulnerabilities and misconfigurations on web servers. It is designed to perform comprehensive tests on web servers and web applications, providing valuable information to system administrators and security professionals about potential weaknesses that could be exploited by attackers.
Why We need to do this nikto ?
Using Nikto is essential for several reasons, especially when it comes to securing web servers and web applications. Here are key reasons why using Nikto is beneficial:
- Vulnerability Identification:
- Comprehensive Scanning: Nikto performs comprehensive scans of web servers, identifying a wide range of vulnerabilities, misconfigurations, and potential security issues.
- Outdated Software: It highlights outdated software versions, web application frameworks, and third-party components that may have known vulnerabilities.
- Risk Mitigation:
- Proactive Security Measures: Identifying vulnerabilities early allows system administrators and security professionals to take proactive measures to address and mitigate potential risks.
- Configuration Checks:
- Server Configuration: Nikto checks for common server misconfigurations, ensuring that servers are set up securely and according to best practices.
- SSL/TLS Security Assessment:
- Cryptographic Weaknesses: It assesses the security of SSL/TLS configurations, helping identify cryptographic weaknesses that could be exploited by attackers.
sudo apt install nikto
sudo nikto -h example.com11. Disable the ServerSignature Directive in Apache
What is ServerSignature Directive in Apache ?
The ServerSignature directive in Apache HTTP Server is used to control the information included in the server’s response headers. These headers are sent to clients in the server’s response to HTTP requests. The ServerSignature directive allows administrators to customize the information included in the “Server” header of the HTTP response, which typically discloses the server software and version.
Why We need to do ServerSignature Directive in Apache ?
The ServerSignature directive in Apache is used to configure a trailing footer line under the server-generated documents (e.g. error pages, directory listing etc).
There are a few reasons why you might want to use the ServerSignature directive:
- To provide debugging information: The ServerSignature directive can be used to display information about the Apache configuration, such as the version of Apache and the operating system. This information can be useful for debugging problems with your Apache configuration.
- To provide branding information: The ServerSignature directive can also be used to display custom text or images. This can be used to brand your website or to provide additional information to your visitors.
- To comply with security requirements: Some security requirements may require you to display information about your Apache configuration in order to be considered compliant. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires merchants to display the version of Apache they are using on all public-facing web servers.
ServerSignature Off<Directory /var/www/html>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
ServerSignature Off
</Directory>Save the changes and once again restart Apache for the changes to come into effect.
12. Limit HTTP Methods:
What is Limit HTTP Methods ?
Limiting HTTP methods in Ubuntu typically involves configuring the Apache web server to allow only specific HTTP methods for a particular directory or set of directories. This is a security measure that helps reduce the risk of certain types of attacks.
Why We need to do Limit HTTP Methods ?
Limiting HTTP methods is a security measure that helps mitigate certain types of web vulnerabilities and enhance the overall security of web applications. Here are key reasons why limiting HTTP methods is important:
- Preventing Cross-Site Request Forgery (CSRF) Attacks:
- Limiting the use of methods like
PUTandDELETEhelps prevent CSRF attacks, where an attacker tricks a user into performing actions they did not intend.
- Limiting the use of methods like
- Mitigating Cross-Site Scripting (XSS) Attacks:
- Restricting unnecessary HTTP methods reduces the attack surface and can help mitigate the impact of XSS attacks by limiting the ways in which malicious scripts can interact with the server.
- Enhancing Security for Sensitive Operations:
- For certain directories or endpoints that involve sensitive operations, limiting HTTP methods ensures that only specific, necessary methods are allowed. For example, restricting to
GETandPOSTfor user authentication.
- For certain directories or endpoints that involve sensitive operations, limiting HTTP methods ensures that only specific, necessary methods are allowed. For example, restricting to
Security thread if i ignore this Limit HTTP Methods
If you ignore limiting HTTP methods in your web application, you expose yourself to several security threats and vulnerabilities. Here are potential security risks associated with not implementing restrictions on HTTP methods:
- Cross-Site Request Forgery (CSRF) Attacks:
- Without limiting HTTP methods, your application becomes more susceptible to CSRF attacks, where an attacker tricks a user into performing unintended actions by exploiting their authenticated session.
- Unauthorized Data Modification:
- Allowing methods like
PUTandDELETEwithout proper validation increases the risk of unauthorized modifications to data. Attackers could manipulate or delete critical information.
- Allowing methods like
- Cross-Site Scripting (XSS) Exploitation:
- Lack of restrictions on HTTP methods can contribute to the impact of XSS attacks. Attackers might exploit vulnerabilities to execute malicious scripts or actions on behalf of authenticated users.
- Information Disclosure:
- Certain HTTP methods, like
TRACE, can be exploited to perform information disclosure attacks. Without restrictions, sensitive data might be inadvertently exposed.
- Certain HTTP methods, like
Example :-
Add the Limit and LimitExcept directives to restrict methods:
<Directory /var/www/html>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
<LimitExcept GET POST HEAD>
Deny from all
</LimitExcept>
</Directory>
13. Enable HTTP Strict Transport Security (HSTS) for Apache
What is HTTP Strict Transport Security (HSTS) ?
HTTP Strict Transport Security (HSTS) is a policy mechanism that protects websites from man-in-the-middle attacks & cookie hijacking. This happens when attackers downgrade the HTTPS protocol to the insecure HTTP protocol. HSTS enables the web server to strictly declare that web browsers should only interact with it via HTTPS, and never through the HTTP protocol.
Why We need to do HTTP Strict Transport Security ?
HTTP Strict Transport Security (HSTS) is a crucial security mechanism that enhances the security of web applications by enforcing secure connections over HTTPS. Here are key reasons why implementing HSTS is essential:
- Mitigating Man-in-the-Middle Attacks:
- HSTS helps mitigate man-in-the-middle (MITM) attacks by ensuring that communication between the client and the server is encrypted using HTTPS. It prevents attackers from intercepting and tampering with sensitive data during transmission.
- Preventing SSL Stripping Attacks:
- SSL stripping attacks involve downgrading a secure HTTPS connection to an unencrypted HTTP connection. HSTS prevents such attacks by enforcing the use of HTTPS, even if a user attempts to access the site using an insecure link.
- Enhancing Data Confidentiality:
- By enforcing the use of HTTPS, HSTS ensures the confidentiality of data transmitted between the client and the server. This is critical for protecting sensitive information such as login credentials, personal details, and financial data.
- Protecting Against Cookie Hijacking:
- Cookies transmitted over HTTPS are more secure than those transmitted over HTTP. HSTS helps protect against cookie hijacking by ensuring that secure cookies are used and transmitted only over encrypted connections.
How to implement HTTP Strict Transport Security (HSTS) in Apache?
Implementing HTTP Strict Transport Security (HSTS) in Ubuntu involves configuring your Apache web server to send the HSTS header in the response. Here are the steps to implement HSTS:
A. Open your Apache configuration file:
sudo nano /etc/apache2/apache2.confB. Add the HSTS Header:
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
</IfModule>
max-age: Specifies the duration (in seconds) that the browser should remember to enforce HTTPS. In this example, it’s set to one year.includeSubDomains: Optional directive to include subdomains in the HSTS policy.- Restart the server.
sudo service apache2 restart
14. Implement Content Security Policy (CSP):
What is Content Security Policy ?
Content Security Policy (CSP) is a security standard that helps protect web applications from various types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. CSP allows web developers to define a set of policies that control which resources can be loaded and executed on a web page, mitigating the risks associated with unauthorized or malicious content.
Why We need to do Content Security Policy (CSP) ?
Implementing Content Security Policy (CSP) is essential for several reasons, all of which contribute to enhancing the security posture of web applications:
- Mitigation of Cross-Site Scripting (XSS) Attacks:
- XSS attacks involve injecting and executing malicious scripts in the context of a user’s browser. CSP helps prevent these attacks by allowing developers to define policies that restrict the execution of scripts to trusted sources, minimizing the risk of unauthorized code execution.
- Protection Against Data Injection Attacks:
- CSP helps protect against data injection attacks, where attackers attempt to inject malicious data into a web page. By defining policies for allowed content sources, CSP reduces the risk of including unauthorized content that could compromise the integrity of the application.
- Reduction of Attack Surface:
- By whitelisting trusted sources for various types of resources (scripts, stylesheets, images, etc.), CSP reduces the attack surface of a web application. This limits the potential entry points for attackers attempting to inject malicious content.
- Prevention of Mixed Content Issues:
- Mixed content issues arise when a web page served over HTTPS includes resources (e.g., scripts or images) loaded over HTTP. CSP includes directives like
upgrade-insecure-requeststo automatically upgrade insecure requests to secure ones, preventing mixed content issues.
- Mixed content issues arise when a web page served over HTTPS includes resources (e.g., scripts or images) loaded over HTTP. CSP includes directives like
Security thread if i ignore Content Security Policy
Ignoring Content Security Policy (CSP) introduces several security threats and vulnerabilities to your web application. Here are potential risks associated with neglecting the implementation of CSP:
- Increased Risk of Cross-Site Scripting (XSS) Attacks:
- Without CSP, your web application is more susceptible to XSS attacks. Attackers can inject and execute malicious scripts in the context of a user’s browser, leading to unauthorized actions, data theft, and other security compromises.
- Data Injection and Content Spoofing:
- Lack of CSP increases the risk of data injection attacks, where attackers inject malicious content into a web page. This can lead to content spoofing, unauthorized modifications, and a compromised user experience.
- Uncontrolled Resource Loading:
- Without CSP, there is limited control over the loading of external resources such as scripts, stylesheets, and images. This opens up opportunities for attackers to load unauthorized content, potentially leading to security vulnerabilities.
Exaxmple :- go to .htaccess file do as below.
# In .htaccess
<IfModule mod_headers.c>
Header always set Content-Security-Policy "your-csp-directives"
</IfModule>15. Disable Server-Side Includes (SSI):
What is server side SSL ?
Server-side SSL (Secure Sockets Layer) refers to the implementation of SSL/TLS protocols on the server side of a communication channel. SSL/TLS are cryptographic protocols that provide secure communication over a computer network, commonly used for securing web traffic on the internet.
Why We need to do server side SSL ?
Implementing server-side SSL (Secure Sockets Layer) or its successor, TLS (Transport Layer Security), is crucial for several reasons, all of which contribute to securing the communication between clients and servers:
- Data Encryption:
- Why? To protect sensitive information.
- How? SSL/TLS encrypts data exchanged between the client and server, making it unreadable to unauthorized parties. This ensures that sensitive information, such as login credentials, personal details, and financial data, remains confidential.
- Data Integrity:
- Why? To prevent data tampering during transmission.
- How? SSL/TLS ensures the integrity of the data by using cryptographic algorithms to detect any modifications or tampering that may occur during transit. This guarantees that the data received by the server is the same as what the client sent.
- Authentication:
- Why? To verify the identity of the server.
- How? SSL/TLS uses digital certificates to authenticate the identity of the server. These certificates are issued by trusted Certificate Authorities (CAs). When a client connects to a server, it can verify the authenticity of the server by checking its digital certificate.
Security thread if i ignore server side SSL
Ignoring server-side SSL introduces several security threats and vulnerabilities to your web applications and communication channels. Here are some significant security risks associated with not implementing server-side SSL:
- Data Interception (Eavesdropping):
- Risk: Without SSL, data transmitted between the client and server is exposed and can be intercepted by attackers.
- Impact: Attackers can eavesdrop on sensitive information, including login credentials, personal details, and financial transactions.
- Man-in-the-Middle Attacks:
- Risk: Lack of encryption allows for man-in-the-middle attacks, where an attacker intercepts and potentially alters the communication between a client and a server.
- Impact: Attackers can modify or inject malicious content into the communication, leading to unauthorized access, data tampering, or the introduction of malware.
- Data Tampering:
- Risk: Unencrypted data is susceptible to tampering during transit.
- Impact: Attackers can modify the content of the communication, leading to potential data corruption, unauthorized access, or injection of malicious code.
Example :- Install the mod_ssl module:
Edit your Apache configuration:
sudo a2enmod ssl
sudo systemctl restart apache2
<VirtualHost _default_:443>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /path/to/your/certificate.crt
SSLCertificateKeyFile /path/to/your/private-key.key
SSLCertificateChainFile /path/to/your/chain-file.pem
# Other SSL configurations (optional)
</VirtualHost>
Enable the SSL Site:
sudo a2ensite default-ssl
sudo systemctl restart apache2
16. Restrict Access to Sensitive Directories in Apache
Another security measure you might take is to limit access to directories that might contain sensitive information such as user data, logs, and configuration files.
<VirtualHost *:80>
ServerName example.com
DocumentRoot /var/www/html
# Other virtual host settings
<Directory /var/www/html/sensitive_directory>
Require all denied
</Directory>
</VirtualHost>17. Disable the server-status Directive
What is Server-status Directive ?
The ServerStatus directive is part of the Apache HTTP Server’s mod_status module. This module provides a way to monitor the performance and status of an Apache server in real-time through a web interface. The ServerStatus directive is used to enable or disable this feature.
Why We need to do Server-status Directive ?
There are a few reasons why you might want to use the Server-status directive:
- To monitor the performance of your Apache server: The Server-status page can be used to monitor the performance of your Apache server and to identify any potential problems. For example, if you see that the number of workers is high and the number of requests being served is low, it could indicate that your Apache server is overloaded.
- To troubleshoot problems with your Apache server: The Server-status page can also be used to troubleshoot problems with your Apache server. For example, if you are seeing errors in your Apache logs, you can check the Server-status page to see if there are any problems with the Apache configuration.
- To provide information to your users: The Server-status page can also be used to provide information to your users about the status of your Apache server. For example, you could display the Server-status page on a maintenance page to let your users know that your server is being updated.
Security thread if i ignore Server-status Directive
Ignoring security considerations for the ServerStatus directive in Apache’s mod_status module can introduce several security threats and risks to your server. Here are potential security threads if you neglect the proper configuration and protection of the server status page:
- Information Leakage:
- Risk: The server status page provides detailed information about the server’s current state, active connections, and worker threads.
- Impact: Attackers can leverage this information to gather intelligence about your server’s architecture, usage patterns, and potentially identify vulnerabilities.
- Resource Exhaustion Attacks:
- Risk: Unrestricted access to the server status page can be exploited by attackers to perform resource exhaustion attacks.
- Impact: Continuous requests to the server status page, especially by automated tools or malicious actors, can lead to increased server load, degraded performance, and potential denial-of-service (DoS) conditions.
- Brute Force Attacks:
- Risk: If the server status page is accessible without proper authentication, it becomes a potential target for brute force attacks.
- Impact: Successful brute force attacks can lead to unauthorized access to the server status information, allowing attackers to gather sensitive details about your server.
Example :- implementation
- Main configuration file:
/etc/apache2/apache2.confor/etc/apache2/httpd.conf - Additional configuration files:
/etc/apache2/sites-available/
Open the Apache Configuration File:
sudo nano /etc/apache2/apache2.conf
Enable the mod_status Module:
<Location "/server-status">
SetHandler server-status
Require local
Require ip 192.168.1.2 # Add your trusted IP addresses
AuthType basic
AuthName "Apache Status"
AuthUserFile /path/to/your/.htpasswd
Require valid-user
</Location>
Save and Restart Apache:
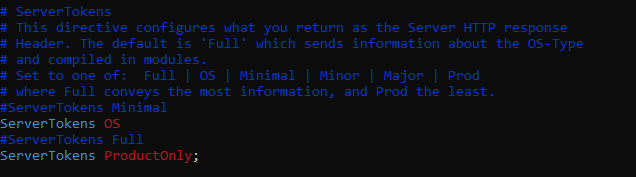
sudo systemctl restart apache218. Disable ServerTokens
What is ServerTokens ?
A server token is a unique identifier that is generated by a server and sent to a client in the response header. It can be used by the client to identify the server and to track the progress of a request.
Server tokens are often used by web servers, such as Apache and Nginx, to identify the server and to provide information about the server configuration. For example, the server token can be used to identify the version of the web server, the operating system that the web server is running on, and the modules that are loaded.
Why We need to do ServerTokens ?
Configuring the ServerTokens directive in Apache is a security best practice aimed at reducing information disclosure and minimizing the attack surface of your web server. Here are some reasons why adjusting ServerTokens is important:
- Security Through Obscurity:
- Reducing the level of information disclosed by the server in response headers follows the principle of “security through obscurity.” By limiting the exposure of specific server details, you make it more challenging for potential attackers to gather information about your server’s software and version.
- Mitigating Targeted Attacks:
- Detailed server information in response headers can be exploited by attackers looking for known vulnerabilities associated with specific software versions. Limiting the information disclosed helps mitigate targeted attacks that rely on precise knowledge of server software versions.
- Minimizing Footprint:
- Exposing unnecessary information about your server’s software and configuration increases the server’s footprint, providing attackers with more data points to analyze. Minimizing this footprint is part of a defense-in-depth strategy.
Security thread if i ignore ServerTokens
Ignoring the configuration of ServerTokens in Apache and leaving it at its default setting (usually set to Full) can introduce several security risks and potential attack vectors. Here are the security threats associated with not configuring ServerTokens:
- Information Disclosure:
- Risk: The default setting (
Full) discloses detailed information about the Apache version and the operating system in response headers. - Impact: Attackers can use this information to identify potential vulnerabilities associated with specific software versions, increasing the risk of targeted attacks.
- Risk: The default setting (
- Targeted Exploitation:
- Risk: Attackers often target known vulnerabilities associated with specific software versions.
- Impact: Without reducing information disclosure, attackers can more easily identify and exploit vulnerabilities, especially if your server is running outdated software.
- Enhanced Reconnaissance:
- Risk: Detailed server information aids attackers in reconnaissance efforts to understand the server’s architecture and potential weaknesses.
- Impact: This information can be used to craft more sophisticated attacks tailored to your specific server environment.
Example :-
Main configuration file: /etc/apache2/apache2.conf or /etc/apache2/httpd.conf
# Set ServerTokens to one of the following values:
# Full: ServerTokens Full (default, includes Apache version and OS)
# OS: ServerTokens OS (includes Apache version without OS details)
# Minor: ServerTokens Minor (includes major and minor version)
# Major: ServerTokens Major (includes major version only)
# Prod: ServerTokens Prod (minimal information, only "Apache")
ServerTokens ProductOnly
19. Disable PHP “eval” Function
What is PHP “eval” function ?
The “eval” function in PHP allows code to be executed dynamically at runtime. This function can be dangerous if not used carefully and can allow attackers to execute arbitrary code on your server. To disable the “eval” function, you can add the following line to your php.ini file −
Why We need to do PHP “eval” function ?
The PHP eval() function is a powerful tool that can be used to execute arbitrary PHP code. However, it is also a dangerous function that can be easily exploited by attackers.
There are a few reasons why you might need to use the eval() function:
- To execute dynamic code that is generated at runtime.
- To execute code that is stored in a database or other external source.
- To implement a custom scripting language.
Security thread if i ignore PHP “eval” function
If you ignore the PHP eval() function, you are leaving yourself open to a number of security threats, including:
- Remote code execution: An attacker could use the
eval()function to execute arbitrary PHP code on your server. This could allow them to take control of your server, install malware, or steal data. - SQL injection: An attacker could use the
eval()function to inject SQL code into your database. This could allow them to steal data from your database or even delete it. - Cross-site scripting (XSS): An attacker could use the
eval()function to inject malicious JavaScript code into your web pages. This could allow them to steal cookies, redirect users to malicious websites, or even take control of users’ browsers.
Example :-
Go to php.ini file, open it in a text editor. Add the following line to the end of the file:
disable_functions = eval20. Limit File Upload Size in Apache
What is limit of File upload in Apache ?
Another way of securing your web server is to limit the total size of the HTTP request body sent to the web server from a client. You can set it in the context of server, per-directory, per-file, or per-location.
For instance, if you want to allow file upload to a specific directory, say /var/www/domain.com/wp-uploads directory, and restrict the size of the uploaded file to 4M = 4194304Bytes, add the following directive to your Apache configuration file or .htaccess file.
Why We need to do Limit of File upload ?
There are a few reasons why it is important to set a limit on file uploads:
- Security: Large file uploads can be used to exploit vulnerabilities in web applications. For example, an attacker could upload a large file that contains malicious code. This code could then be executed when the file is processed by the web application.
- Performance: Large file uploads can also have a negative impact on the performance of web applications. This is because the web application has to process the entire file before it can respond to the user.
- Storage: Large file uploads can also consume a lot of storage space on the web server. This can be a problem for websites and applications that have limited storage space.
Security thread if i ignore this Limit of File Upload ?
Ignoring the limitation of file uploads in a web application can expose your system to various security threats and operational challenges. Here are some security threats and concerns that may arise if you ignore or do not properly enforce file upload limits:
- Denial of Service (DoS) Attacks:
- Threat: Without limits, an attacker could flood your server with large file uploads, leading to resource exhaustion and causing a denial of service.
- Impact: Service disruptions, increased server load, and potential unavailability for legitimate users.
- Resource Exhaustion:
- Threat: Unlimited file uploads can quickly consume server resources, including disk space, memory, and bandwidth.
- Impact: Exhaustion of server resources, performance degradation, and increased operational costs.
- Storage Overflow:
- Threat: Large uploads may fill up available storage space on the server.
- Impact: Lack of storage space for other critical services and potential disruption of normal server operations.
- Network Congestion:
- Threat: Unrestricted uploads can lead to significant network traffic, causing congestion.
- Impact: Slower network performance, potential service interruptions, and a degraded user experience.
- Security Vulnerabilities:
- Threat: Large file uploads may be used as a vector for exploiting vulnerabilities in the application or server.
Example :-
Go to Apache configuration file .htaccess file.
<Directory "/var/www/domain.com/wp-uploads">
LimitRequestBody 4194304
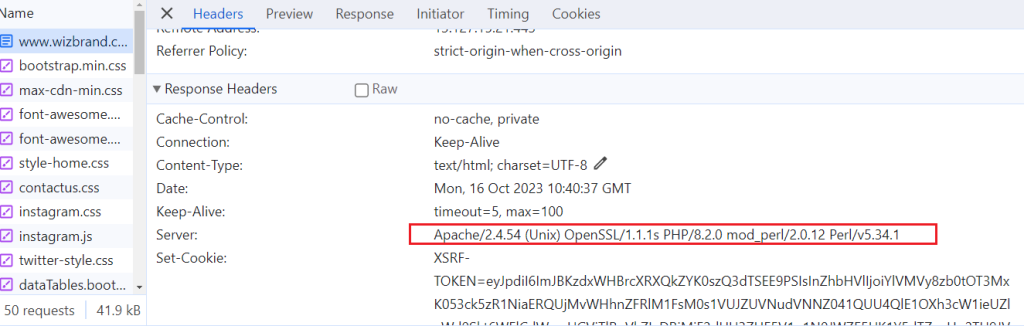
</Directory>21. Server Version Banner should be removed.
What is Server Version Banner ?
The Server Version Banner, also known as the “Server Signature” or “Server Token,” is information that web servers include in their responses to identify the software and version running on the server. This information is often sent in the HTTP response headers. The Server Version Banner typically includes details such as the server name and version number.
Why We need to do Server Version Banner ?
Reasons for Using Server Version Banner:
- Transparency for Developers and Administrators:
- Advantage: The Server Version Banner provides transparency about the server environment for developers and system administrators.
- Use Case: Legitimate users may find it helpful for troubleshooting and ensuring compatibility with specific server versions.
- Compatibility Information:
- Advantage: Developers and users can quickly identify the web server software and its version, ensuring compatibility with specific features and functionalities.
- Use Case: It helps in situations where knowing the server details is essential for proper interaction with the web application.
- Diagnostic Information:
- Advantage: The Server Version Banner can assist in diagnostics, allowing administrators to identify and address server-related issues more effectively.
- Use Case: It aids in understanding the server environment and diagnosing problems related to specific server versions.
Security thread Disable the Server Version Banner
- Disable the server version banner: Most web servers allow you to disable the server version banner. This is the best way to protect yourself from version-based attacks and fingerprinting.
- Upgrade the web server software: Web server software is regularly updated to patch vulnerabilities. By keeping your web server software up to date, you can reduce the risk of being attacked.
- Use a web application firewall (WAF): A WAF can help to protect your web application from a variety of attacks, including version-based attacks and fingerprinting.
Example :-
If you want to disable the server version banner then go to below directory.
/opt/lampp/apache2/conf
- Go to the $Web Server/conf directory.
- Using the vi editor, modify httpd.conf.
- Save the httpd.conf file after adding the following directive.
ServerTokens "Prod"
ServerSignature "Off"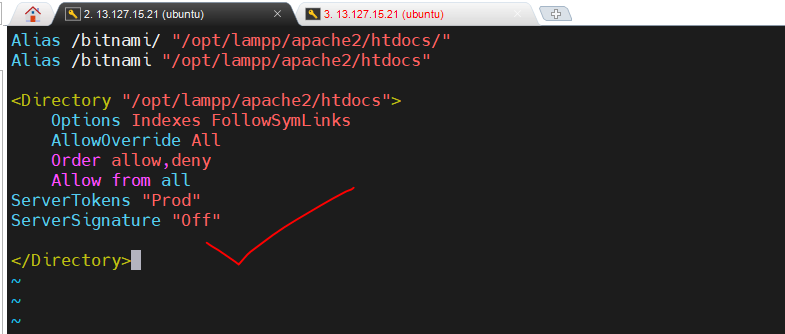
Thanks its helpfull for you…. 👍👍